Malware VS Virus – what is the difference? Describing the phenomenons
The correct definitions of most of the things in the computer world are known, and it is pretty hard to find one that can still be discussable. However, there is one argument that lasts for about a decade – what is the difference between virus and malware?
Huh, to answer this question, we need to have a look at the history of malware and computer viruses. Even the historical timings bring a lot of disagreements. That’s why history is not the only thing that will be looked at – modern facts bring a lot of clarity at this point. Without further interruption – let’s go.
What is so controversial in malware vs virus?
A lot of people falsely think that malware and virus are synonyms. However, they are not the same, and not even similar. In fact, a computer virus is a subcategory of malware – the global term for malicious software. The habit to call malware “viruses” appeared in the ‘00s when viruses (as a subtype of malware) flooded the users’ PCs. That’s why it just turned into a common noun – in one line with Thermos and Xerox.
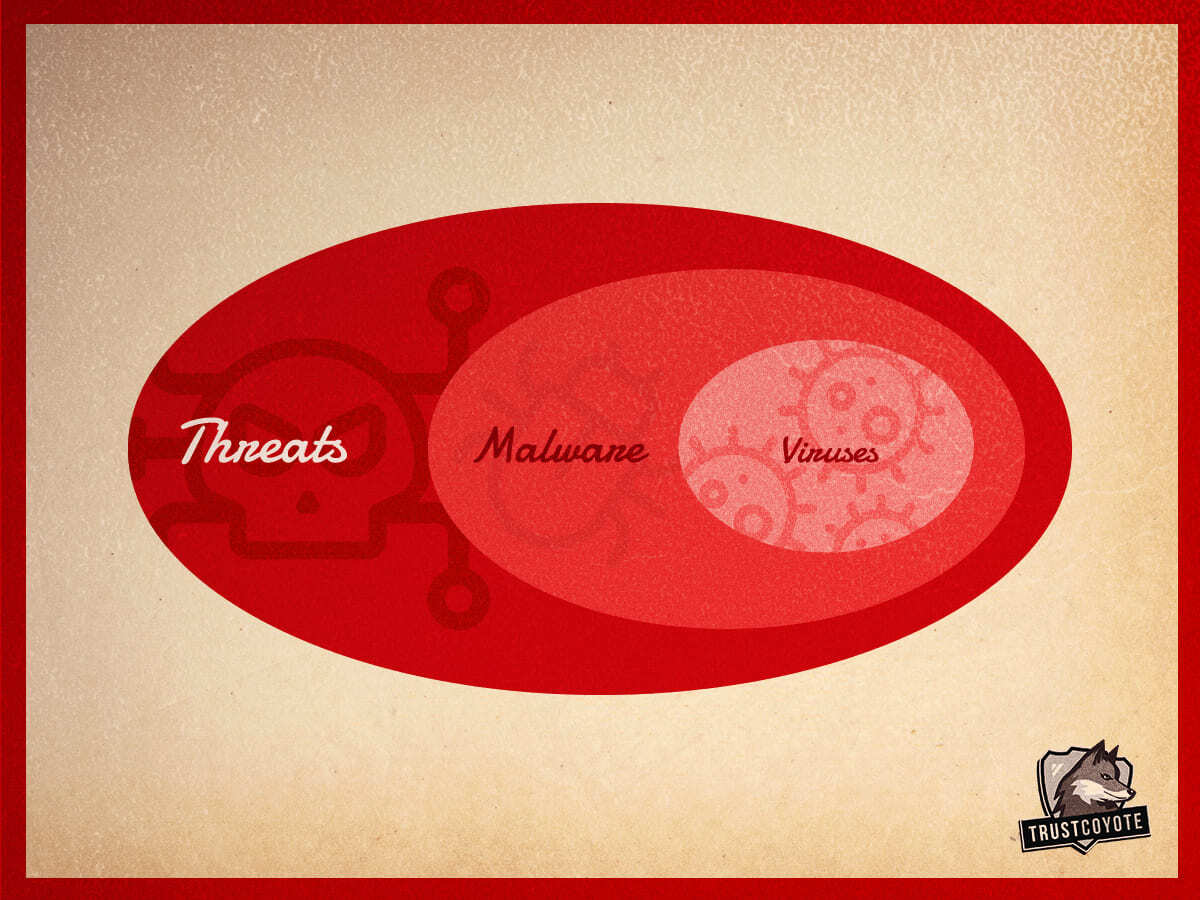
Malware and virus: comparing the phenomenons
Looking into the history
As I have mentioned, certain elements of malware and computer virus history bring a lot of discussions. The term “malware” appeared in 1990 – over 30 years ago. Meanwhile, computer viruses appeared much earlier, and different sources name different years. Someone count the computer virus history since the first mention of the program that can replicate itself. That happened in 1949 – John Newman in his lecture “Theory and Organization of Complicated Automata”1 told about the program that can make the computer inoperable by multiple replications of its code.
First computer virus
In fact, the first working example of a computer virus appeared in 1982 – the so-called Elk Cloner. That virus was infecting the floppy disks with programs, displaying the jokisch poem instead of the program’s interface:
ELK CLONER:
THE PROGRAM WITH A PERSONALITY
IT WILL GET ON ALL YOUR DISKS
IT WILL INFILTRATE YOUR CHIPS
YES IT'S CLONER!
IT WILL STICK TO YOU LIKE GLUE
IT WILL MODIFY RAM TOO
SEND IN THE CLONER!
It was not very widespread – just because of the absence of the Internet in those times, and also because the virus was coded for the Apple II operating system. However, it showed the overall direction of how the viruses will act and look like.
Read also: Hackers don’t like to brute force long passwords
Morris Worm
The first example of a really massive piece of malware appeared 6 years later. In 1988, a Morris Worm kicked on the Internet, which was small and non-global at that point of time. Robert Morris, the computer scientist who created this malware, said that he created it “just to see if it will work”. And it did – and started the phenomenon of malware, which still gives a sensible push to the cybersecurity industry.

The floppy disk with the source code of Morris’ worm
Morris worm was designed for the 4BSD operating system. This OS was the predecessor of a modern FreeBSD, macOS and macOS Server2. The worm was exploiting the vulnerabilities present in that version of the OS, primarily – in mailing client, networking protocol and remote-access tools. That was pretty original by that moment of time, but restricted by the single OS version – later versions had these breaches fixed, earlier ones did not have such functionality. Nonetheless, the experiment was very successful – and Morris was awarded the first lawsuit for the felony conviction under the 1986 Computer Fraud and Abuse Act.
Diving into malware
As I have mentioned, the term “malware” appeared in 1990 – shortly after the breaking appearance of Morris Worm. The implementation of this word was not forced – malware was still not so widespread, but in 2-3 years it was a rising star. Why? The first reason why malware was not widespread in the early ‘90s was the absence of mass-market Internet access. Since 1994, the world-wide-web began growing exponentially, which led to a massive surge in the interest in malware.
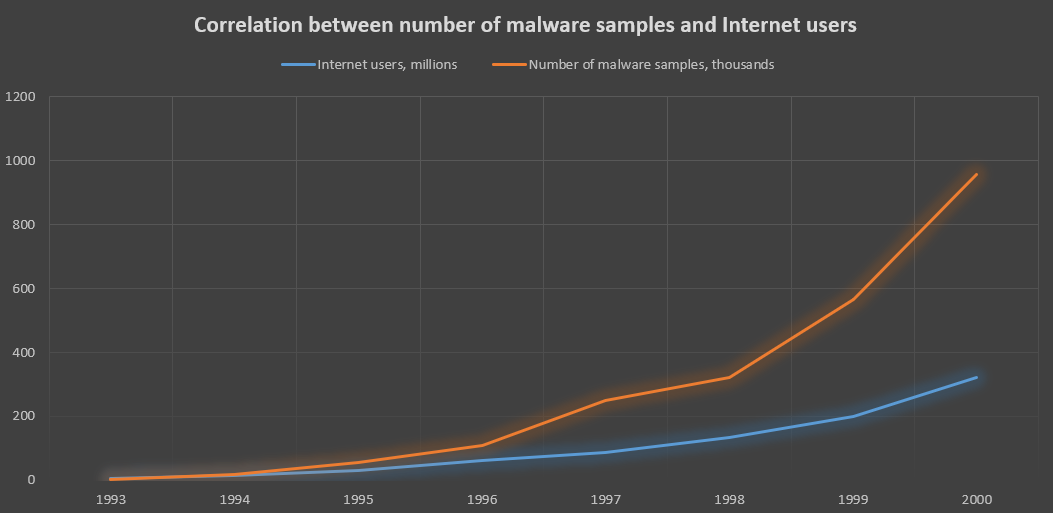
The graph represents the correlation of malware samples number to number of Internet users in the world
First mass-market malicious programs were clumsy, not very reliable, but still effective. Users had literally no experience, and it was extremely easy to trick them to install malware. Moreover, contemporary operating systems were full of different security breaches. Take it and love it – that was the simplest time on the cyber criminality market. Nowadays, only complicated and state-of-art things can really reach tops of the chart – like in a “legal” programming, however.
Simple definition of computer virus
So what is, exactly, the virus? The definition of a computer virus was partially given several paragraphs above, but there is still no clarity about this. So, a computer virus is a program that is able to inject the parts of its own code into other programs, and then call these programs to replicate the virus code, again. These actions lead the infected programs to malfunction, and, finally, system errors. The boom of viruses began approximately in 2000 and kept going almost until 2010. At the edge of the second decade of XX age, malware analysts discovered a way to counteract viruses. The rule which killed viruses as a class of malicious programs dictated that every program that reads the text file as a code is a virus.
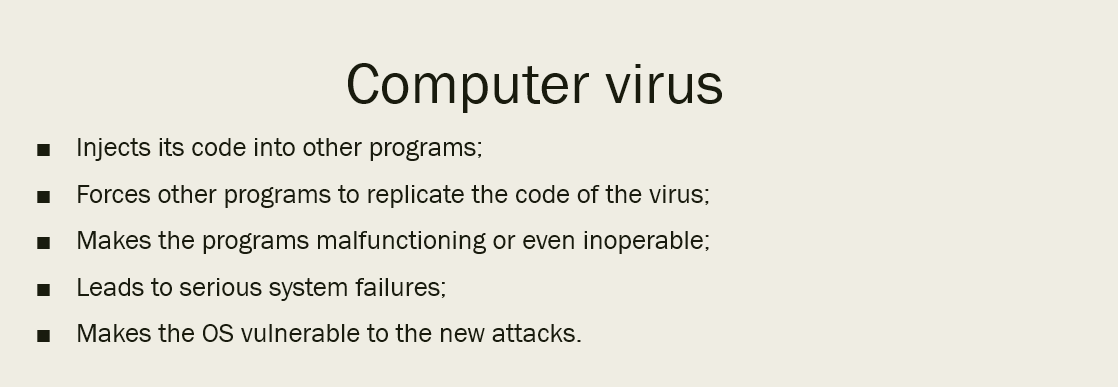
Computer virus definition in several short sentences
Malware vs virus. What is in total?
Malware is a global category that appeared because of the global call – the appearance of malicious programs. The main catalyst for malware spreading was the development of the Internet – it acted as a global pool of possible victims. And poorly protected computers, together with the naivety of users made the malware even easier to manage. The vast majority of modern malicious programs are used to make money on their victims – by showing you ads, stealing your data, or asking for the ransom.
Computer viruses, on the other hand, appeared much earlier than the term “malware”. The first virus that was circulating in the wild appeared in 1992, and a really massive and destructive one – in 1988. The world saw a virus fury in the ‘00s when this type of malware took almost 40% of all malware injection cases. It was used just to mischief the user, as well as the complementary malware – to open the system for further virus injections. Around 2010, however, computer viruses suddenly ceased to exist – anti-malware program developers discovered the way to defeat all viruses together by a single rule.
How to protect your system against malicious programs?
Modern malicious programs are extremely flexible. The eternal chase – cybersecurity analysts against malware creators – is going almost two decades, since the antivirus programs invention. The proper security software is obligatory if you want to have a secured system. But which one can be called proper? And which one corresponds to what it is offering on the official website?
The typical “catch” of a good anti-malware software
We did several tests of antivirus software this year. Exactly, we chose ones that can provide you the full protection without any excessive functions. These programs have often database updates, and proactive protection as an obligatory function – it is a must-have to stop malicious things even before they start the action. The table at the end of this article will definitely help you to figure out what is best for you. Do not rely on Defender – it showed itself too bad and vulnerable!
- Read the lecture transcription – that will be very interesting if you want to know more about how the computers were invented.
- The genealogic tree of Berkeley Software Distribution (BSD) operating systems.












