Researchers Created a TickTock Device to Detect Wiretapping
Experts from the National University of Singapore and Yonsei University have developed a TickTock device to detect wiretapping. TickTock can check if the microphone of a laptop or smartphone is being used to secretly record user conversations.
Let me remind you that we also wrote that Apple Introduces Lockdown Mode to Protect against Spying.
The device is based on the Raspberry Pi 4 Model B, but in the future, they want to make it look like a regular USB flash drive.
The gadget and the process of its creation are described in detail in a document published on ArXiv. The authors of the development note that remote “spy” attacks are becoming more and more frequent, but if security measures have been developed for webcams for a long time (or you can always cover the camera with electrical tape, as Mark Zuckerberg does), there are no similar barriers to prevent listening.
The document says that laptop manufacturers have recently been trying to make microphone activation more obvious to the user and impossible for malware. For example, Apple devices have introduced a hardware microphone mute designed to block the microphone when the lid is closed.
In 2020, Dell has added microphone and camera privacy drivers to Linux. Windows 10 and macOS 12 have visible microphone activation indicators, and Purism has built a hardware switch for the microphone and camera into its privacy-focused Librem 5 USA smartphone.
The researchers write that all of these approaches have disadvantages:
The TickTock prototype assembled by scientists consists of near-field sensors, an RF amplifier, an SDR, and a Raspberry Pi 4 Model B. At the same time, the experts write that the final form of the device will be more like a USB flash drive that can be put next to a laptop or banned on it so that the gadget can alert the user of any changes in the state of the device’s microphone.
The way TickTock works is quite simple: it relies on the fact that MEMS microphones on regular laptops emit electromagnetic signals when they are active and active.
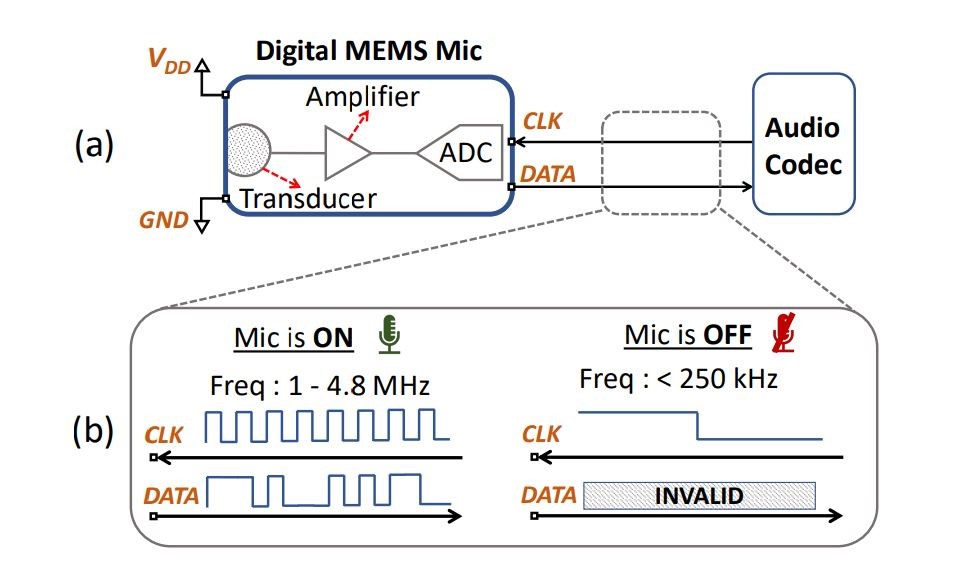
During the creation of TickTock, the researchers faced a number of problems. First, the clock frequency varies depending on the audio codec chip in a particular laptop. Secondly, the area of the laptop where the strongest EM signal will leak depends on the model and configuration of the device. Third, not all captured EM signals will be indicative of microphone activity, they can also come from other circuits, and this needs to be filtered out to prevent false alarms.
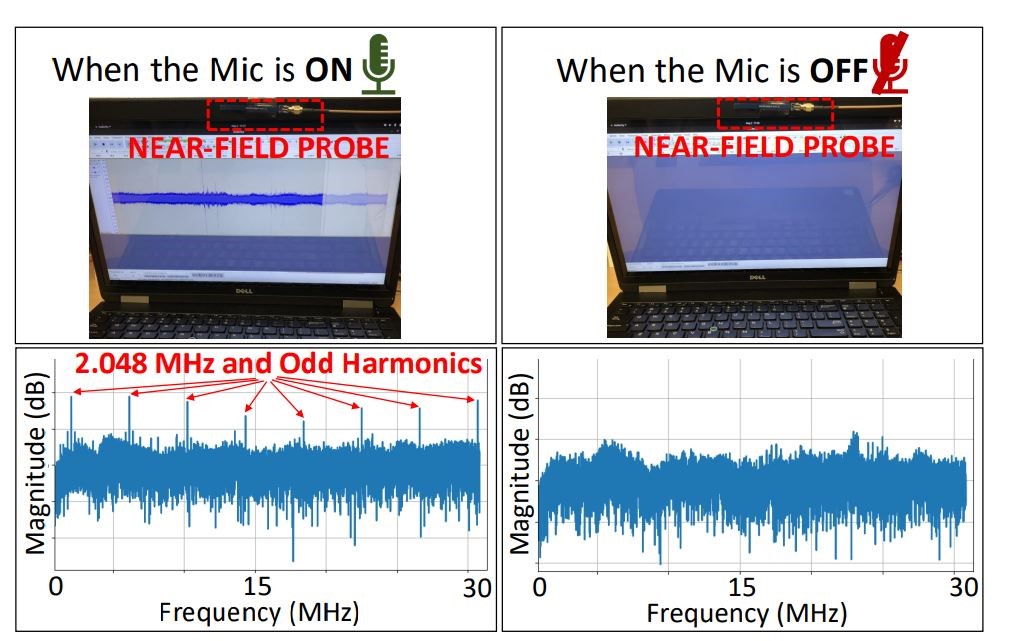
For these reasons, TickTock performed well on about 90% of the laptops tested (including various Lenovo, Dell, HP, and Asus models), but it failed to detect microphone activity on three Apple MacBook laptops. The aluminum cases and short, flexible cables of Apple devices dampen electromagnetic signal leakage to the point where TickTock cannot detect it.
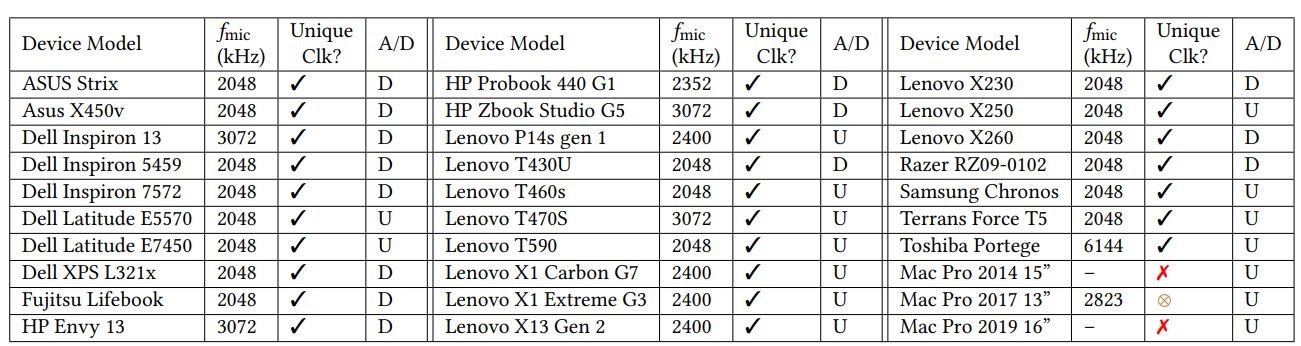
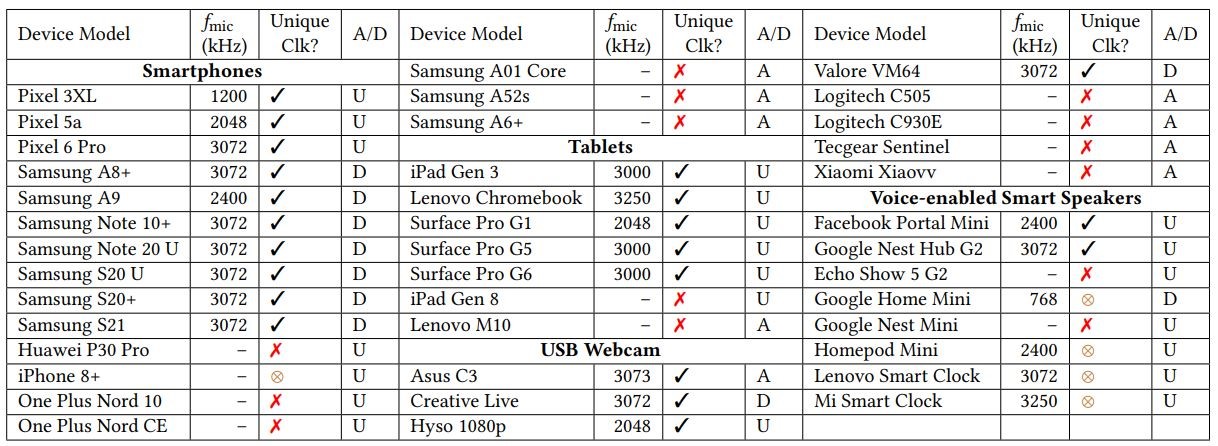
TickTock was also used for search of wiretapping on 40 other devices, including smartphones, tablets, smart speakers and USB webcams. The gadget was able to detect microphone activity on 21 devices out of 40. The high failure rate is likely due to the use of analogue rather than digital microphones in some smartphone models, as well as the fact that small equipment more often relies on shorter wires, which reduces electromagnetic radiation.
In the future, experts plan to expand the functionality of TickTock so that the device can also detect unauthorized access to cameras and inertial sensor units.










