Hackers rarely brute-force passwords longer than 7 characters
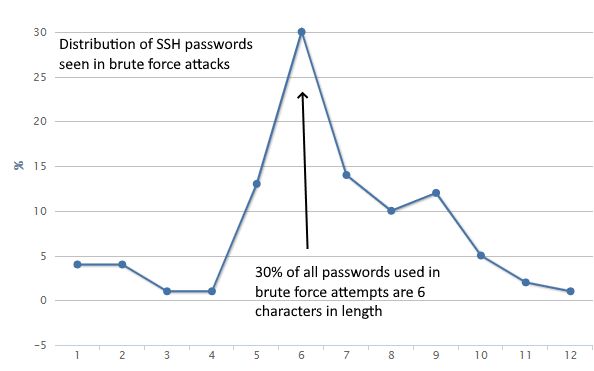
Microsoft cybersecurity specialist shared some interesting statistics: most cybercriminals prefer to brute-force passwords no longer than 7 characters, and only a small percentage of attacks target long passwords containing special characters.
The researcher collected statistics for this analysis from numerous honeypot servers, which he manages on duty, studying the trends among attackers:
The expert also writes that only in 7% of cases at least one special character was used during brute force attacks, while in 39% of cases at least one digit was used. At the same time, none of the brute-force attempts took into account passwords, which may contain spaces.
The results of this study demonstrate that longer passwords containing special characters are more likely to be protected from the vast majority of such attacks. Of course, unless the credentials are otherwise “leaked” to the public and are not included in special dictionaries and malicious lists. Such leaks are usually related to spyware activity – so be careful and use anti-spyware programs for better security.
Bevington notes that based on data from 14 billion brute-force attacks on Microsoft honeypot servers, attacks on RDP have tripled since 2020, by 325%. In addition, attacks on Network printing services, as well as Docker and Kubernetes, increased by 110% by 178%.
Let me remind you that I also wrote that Researchers taught the algorithm to guess PIN-codes from bank cards.