New White Phoenix Tool Helps Recover Files Partially Encrypted by Ransomware
Security experts have created White Phoenix, a new tool for decrypting files affected by ransomware attacks.
White Phoenix will allow victims to partially recover files encrypted by malware that uses discontinuous encryption. The tool is already available for free download on GitHub.
Let me remind you that we also wrote that Free Decryptor Arrived for MegaCortex Ransomware, and also that Search for Random Leaks of API Keys, Passwords and Tokens Works for All GitHub Users.
Breakthrough encryption is a technique used by some ransomware groups. The idea is that the malware alternately encrypts and does not encrypt data fragments, which allows the file to be encrypted much faster, making the data unusable by the victim.
In the fall of 2022, Sentinel Labs reported that discontinuous encryption is gaining momentum, all major RaaS (Ransomware-as-a-Service) already offer it at least as an option, and the BlackCat/ALPHV ransomware has the most complex implementation.
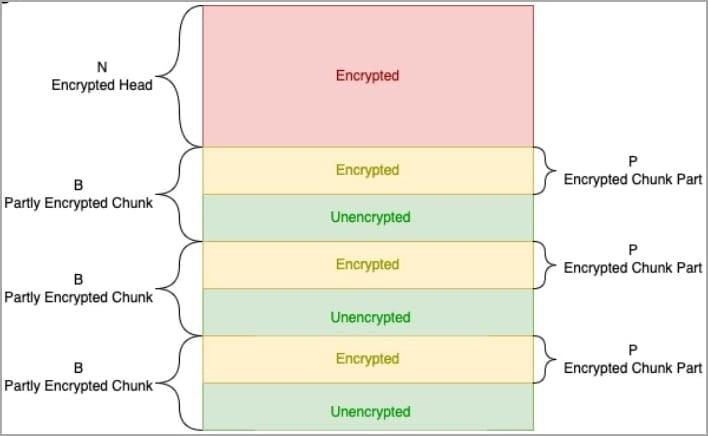
Discontinuous Encryption in BlackCat
Currently, ransomware using discontinuous encryption includes BlackCat, Play, ESXiArgs, Qilin/Agenda, and BianLian.
Let me remind you that the media said that BlackCat Group Leaks Western Digital Data to the Network.
Breaking encryption creates weaknesses because leaving parts of the original files unencrypted opens up the possibility of free data recovery, as CyberArk, who developed White Phoenix and released it to the public, now says.
CyberArk developed White Phoenix after experimenting with partially encrypted PDFs in an attempt to recover text and images from streaming objects. As a result, the researchers found that in some BlackCat encryption modes, many objects in PDF files remain unchanged, which allows data to be extracted.
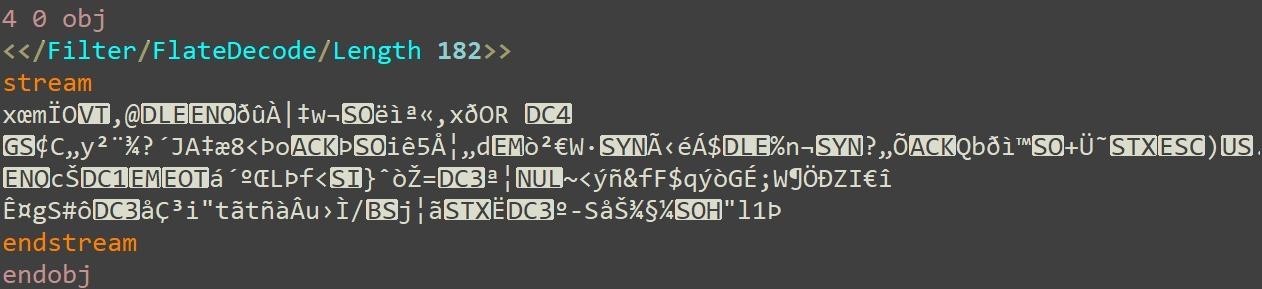
So, in the case of images, restoring them turned out to be as easy as removing the applied filters. In the case of working with text, recovery methods include identifying text fragments in streams, combining them, or reversing hex encoding and CMAP scrambling.
After successfully recovering PDF files, CyberArk analysts found that it is possible to recover files of other formats in a similar way, including those based on ZIP. Such files using the ZIP format include: Word (docx, docm, dotx, dotm, odt), Excel (xlsx, xlsm, xltx, xltm, xlsb, xlam, ods) and PowerPoint (pptx, pptm, ptox, potm, ppsx , ppsm, odp).
Recovery of these file types is achieved using 7zip and a hex editor to extract unencrypted XML files from affected documents and perform data replacement. White Phoenix automates the above steps for supported file types, although in some cases it may still require human intervention.
Analysts say that their tool should work well with the specified file types encrypted by the following ransomware: BlackCat/ALPHV, Play, Qilin/Agenda, BianLian, DarkBit.
At the same time, it is emphasized that White Phoenix does not always guarantee an acceptable result, even if it works with a supported file type. For example, if most of the file is encrypted, including its important components, the recovered data may be incomplete or useless. That is, the effectiveness of the tool is directly related to the degree of data corruption.













Mantap jika sdh ada tools utk memperbaiki data yg di rusak ransomeware