Fake antivirus promised protection from Pegasus spyware, but turned out to be a Trojan
Attackers are eager to take advantage of the recent Pegasus spyware scandal and have even released a fake antivirus.
Under the guise of a security scanner that looks for traces of Pegasus in the system, hackers are distributing RAT Sarwent.
Let me remind you that in June 2021, the human rights organization Amnesty International, the non-profit project Forbidden Stories, as well as more than 80 journalists from a consortium of 17 media organizations in ten countries of the world published the results of a joint investigation, which was named the Pegasus project. Then the experts said that they had discovered large-scale abuse of the Pegasus spyware, created by the Israeli company NSO Group. According to their report, the company’s spyware is actively used to violate human rights and to monitor politicians, activists, journalists and human rights defenders around the world.
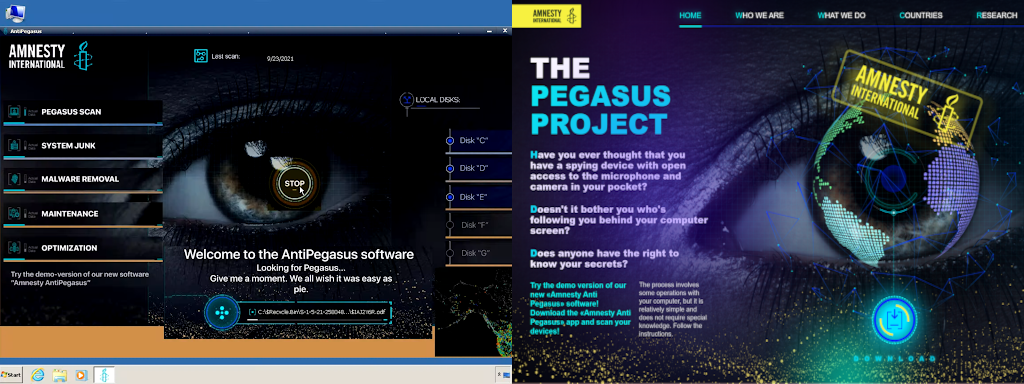
Cisco Talos experts report that attacks using Sarwent have been carried out since the beginning of this year, and they target the most victims in several countries around the world. What decoys were used by the attackers in past campaigns is unknown, but now analysts have discovered that Sarwent is being distributed through the fake Amnesty International website and advertised as a defensive solution against Pegasus. In fact, the malware tried to make it look like a real antivirus, even developing an appropriate graphical interface.
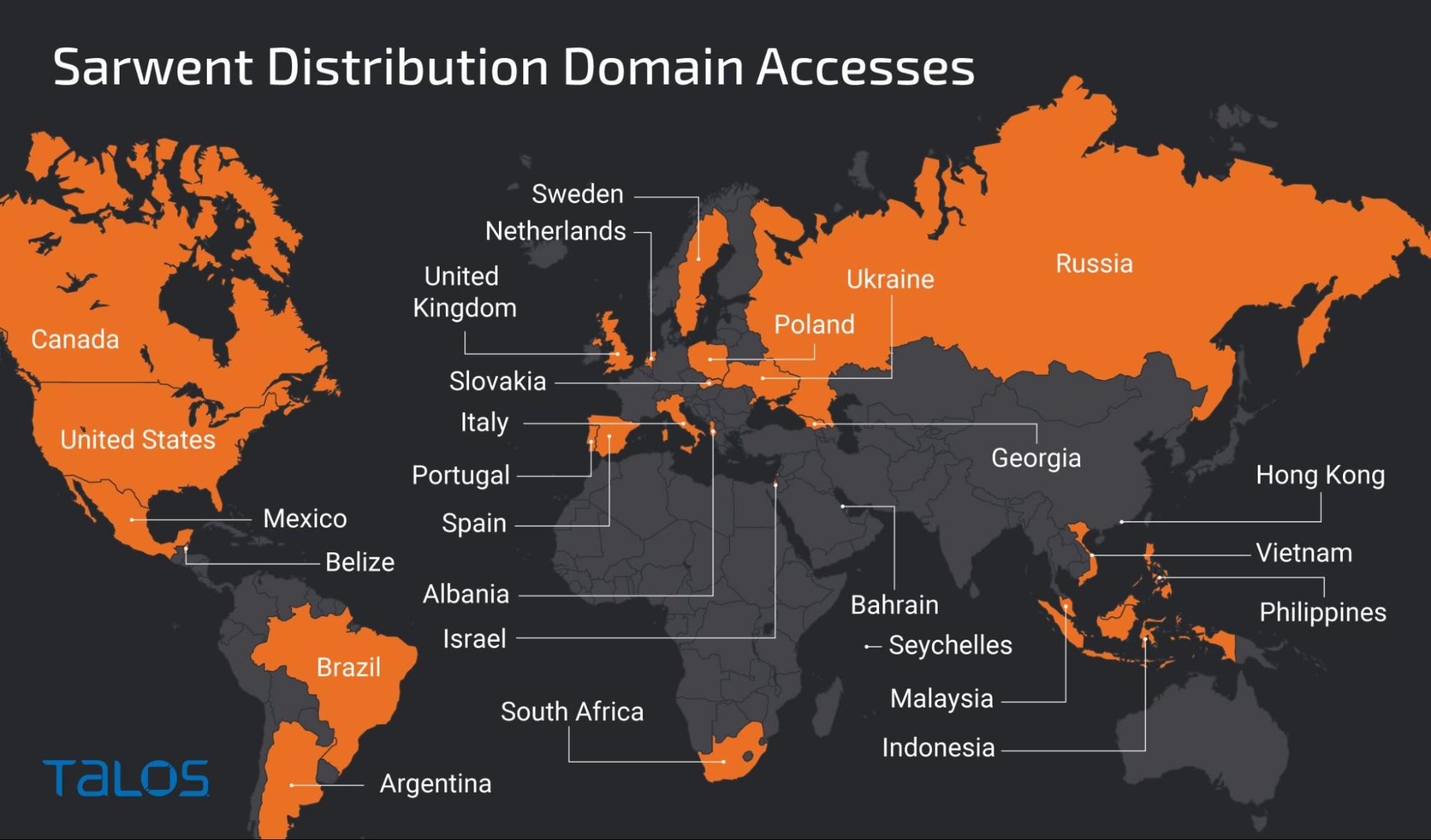
While researchers have not figured out exactly how hackers are luring visitors to this fake site, an analysis of the campaign’s domains showed they were being accessed by users from all over the world, although no sign of a large-scale campaign was found.
In addition to copies of the Amnesty International website, Sarwent has also registered the following domains:
- amnestyinternationalantipegasus [.] com;
- amnestyvspegasus [.] com;
- antipegasusamnesty [.] com.
Experts are confident that a Russian-speaking attacker is behind this campaign. Also, the specialists managed to find a similar backend that has been used since 2014. This suggests that either Sarwent is much older than previously thought, or that other hackers have used it in the past.
Sarwent is written in Delphi, which is not common among modern malware. Like other RATs, it provides its operators with access to the infected machine. It provides direct access to the system by activating RDP or via Virtual Network Computing (VNC). However, malware can use other methods, including shells and PowerShell execution.
Researchers are not yet sure whether Sarwent’s operators are pursuing financial gain, or whether it is, for example, espionage. Same uncertainty remains with the distribution ways. Some analysts say Sarwent RAT may mimic some legit applications, or even DLLs – like VulkanRT or .NET Framework-related ones.
Let me remind you that I also talked about the fact that Avast specialists discovered a fake version of Malwarebytes antivirus.












