Microsoft and FireEye found three more malware that attacked SolarWinds clients
This week, cybersecurity experts from Microsoft and FireEye published new reports and found three more malware that attacked SolarWinds and its customers.
Last year, it became known that SolarWinds, which develops software for enterprises to help manage their networks, systems and infrastructure, has been compromised. This attack on the supply chain has been attributed to a supposedly Russian-speaking hack group that cybersecurity experts track under the names StellarParticle (CrowdStrike), UNC2452 (FireEye) and Dark Halo (Volexity).
After infiltrating the SolarWinds network, the attackers provided Orion’s centralized monitoring and control platform with a malicious update. As a result, many SolarWinds customers installed an infected version of the platform, therefore letting the hackers into their networks.
Among the victims are such giants as Microsoft, Cisco, FireEye, as well as many US government agencies, including the State Department and the National Nuclear Security Administration.
Previously, experts investigating the incident described four malware that hackers used during this campaign:
- Sunspot – malware that hackers have deployed on the SolarWinds intranet to infiltrate the Orion build process.
- Solorigate (Sunburst) – malware introduced in Orion updates in March-June 2020. It was used for reconnaissance, with its help the attackers identified the companies of interest to them;
- Teardrop – malware deployed by hackers on selected networks via Sunburst, used as a backdoor to execute other commands;
- Raindrop is another minor backdoor deployed to some victims’ networks instead of Teardrop.
This week, cybersecurity experts from Microsoft and FireEye released new reports on three more threats that hackers used during an attack on SolarWinds and its customers. Microsoft’s report covers all three types of malware, while FireEye’s report covers just one of them:
- GoldMax is a Go-based backdoor that hackers used to execute various commands on already compromised systems. The malware is described in detail in the FireEye report SUNSHUTTLE;
- Sibot – VBScript malware designed to ensure a stable presence on infected hosts (three different variants were detected);
- GoldFinger is another malware written in Go. It was used as an HTTP tracker and recorded the routes along which packets get to the control server.
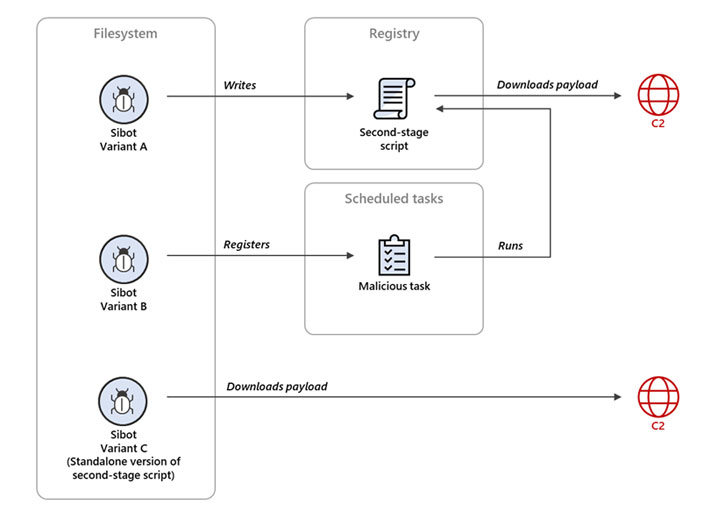
Microsoft says the malware was found on the networks of some of the affected companies that were compromised last year. In some cases, the malware was installed back in June 2020, while in other cases it was used recently, for example, in September 2020.
They introduced malware in different ways. For example, some victims were compromised using the malicious Orion update, while others were infected with the same malware, but after the hackers gained access to the credentials for the company’s internal network.
Microsoft experts say that all of the detected threats are linked to the same attackers were responsible for compromise of the Orion platform. For the first time, the company officially named the hacker group responsible for the attack, giving it the name Nobelium.
“They were designed specifically for certain networks and were only used after attackers gained access [to the victim’s network] using compromised credentials or the SolarWinds binary, and after lateral movement using TEARDROP and other manual actions”, – Microsoft explained.
According to Microsoft analysts, at all stages of the attack, attackers demonstrated profound knowledge of the software tools, structures, security solutions prevalent in such systems networks, as well as the methods of work often used by incident response teams. This knowledge was reflected in the operational decisions of the attackers, from the choice of C&C infrastructures to the names of the scheduled tasks used to maintain resilience.












