Cybersecurity experts compile lists of companies affected by the SolarWinds hack
Several information security companies have released the lists of companies affected by the SolarWinds hack and malware infection of the Orion platform. The victims of hackers include tech companies, local governments, universities, hospitals, banks, telecom operators and many others.
Famous names include Cisco, SAP, Intel, Cox Communications, Deloitte, Nvidia, Fujitsu, Belkin, Amerisafe, Lukoil, Rakuten, Check Point, Optimizely, Digital Reach, and Digital Sense. MediaTek, one of the world’s largest semiconductor manufacturers, is also believed to have been affected, although researchers are not100% sure yet.
Let me remind you that the malware spreading with malicious versions of Orion (released between March and June 2020) was codenamed SUNBURST (aka Solorigate).
According to reports from Microsoft, FireEye, McAfee, Symantec and the US Department of Homeland Security’s Cybersecurity and Infrastructure Protection Agency (DHS CISA), the malware collected information about the victim’s network in infected systems, waited 12-14 days and then sent this data to a remote server of the attackers.
If after that the malware operators recognized the company’s network as interesting, they developed the attack further and continued to collect information.
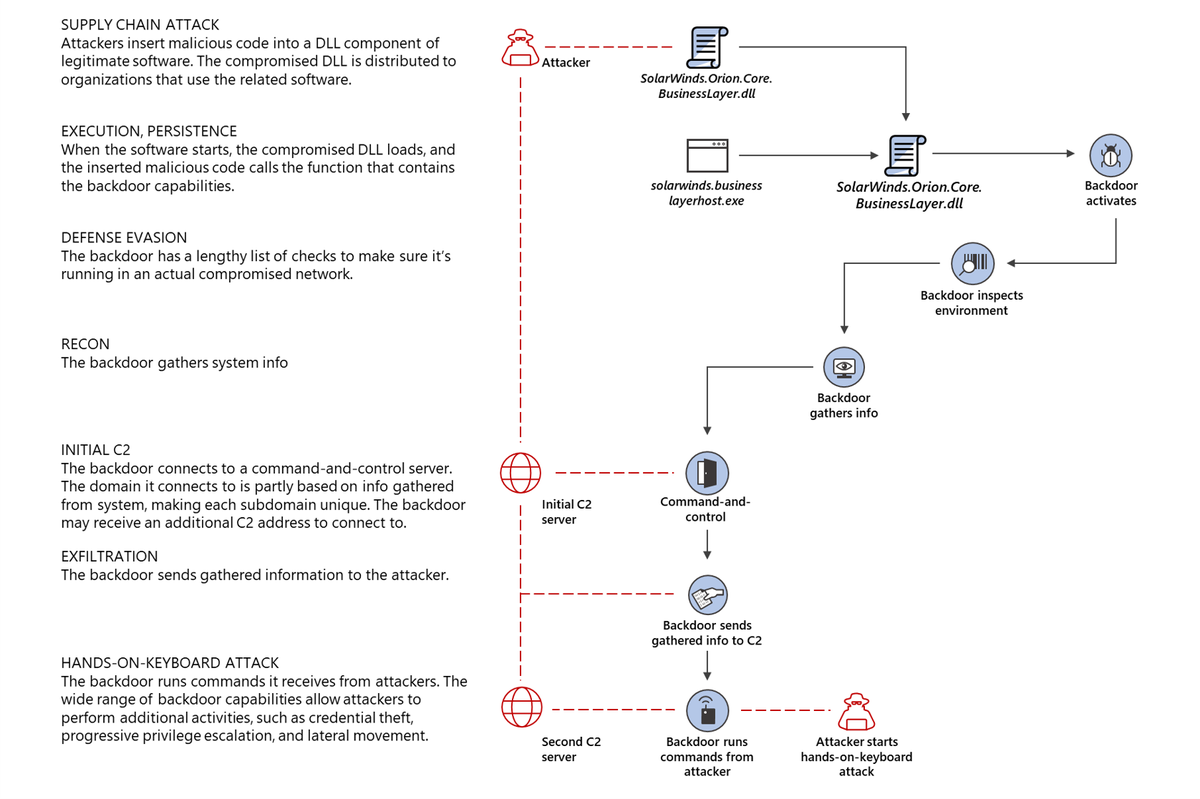
According to official data of the 300,000 SolarWinds customers, only 33,000 were using Orion, and the infected version of the platform was installed in 18,000 customers. Initially, it was believed that only SolarWinds specialists would be able to identify all the victims, but as other experts continued to study the work of SUNBURST, they discovered some important features in the work of the malware. For example, one of them was related to the mechanism of pinging the C&C server.
It turned out that SUNBURST was sending data collected on the infected network to the URL of its C&C server, unique for each victim. The unique URLs were subdomains of avsvmcloud [.] Com and consisted of four parts, the first of which was a seemingly random string. However, security researchers soon noticed that this string was not actually random, but contained the encoded domain name of the victim’s local network.
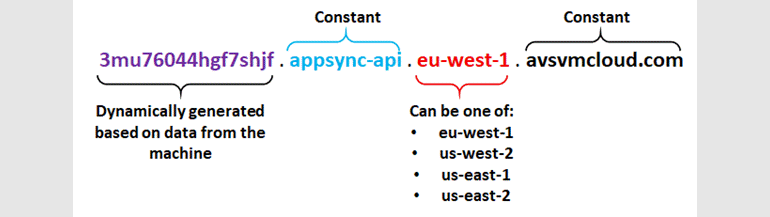
As a result, several companies and independent researchers analysed the traffic history and passive DNS data in order to collect information about avsvmcloud[.]com traffic, detect subdomains, and then calculate the companies that installed the infected versions of Orion
As a result, experts from TrueSec and Prevasio, independent researcher Dewan Chowdhury, and the Chinese firm QiAnXin began publishing lists of affected companies and organizations at the end of last week.
“Despite the compromise of 18,000 SolarWinds customers, the hackers continued to attack only 50 companies“, – said in the FireEye company.
Microsoft experts, in turn, wrote that they were able to identify about 40 victims from among their customers.
“The attack usually proceeded when the avsvmcloud[.]com control server responded to the malware with a specific DNS response with a certain CNAME field”, – told Microsoft experts.
This special field contained the address of the second command and control server, from which SUNBURST could receive additional commands and sometimes download more malware.
At present, only one company, which the hackers continued to hack, is known for certain – this is the information security company FireEye, as its reaction to the attack shed light on the compromise of SolarWinds in general.
ZDNet writes that many in the cybersecurity community are currently working with content delivery networks, Internet service providers and other companies to collect passive DNS data and track traffic avsvmcloud[.]com. All this activity is aimed at identifying other victims, to whose networks cybercriminals could also gain in-depth access.












