FireEye said that there are more than 1900 active hacker groups in the world
The American information security company FireEye has released an annual report, according to which more than 1900 different hacker groups are currently operating are in the world. In 2019, there were about 1,800 of them.
In 2020, experts discovered 650 new hack groups, and also removed about 500 groups from their threat tracker due to duplication and overlap with previously known clusters.
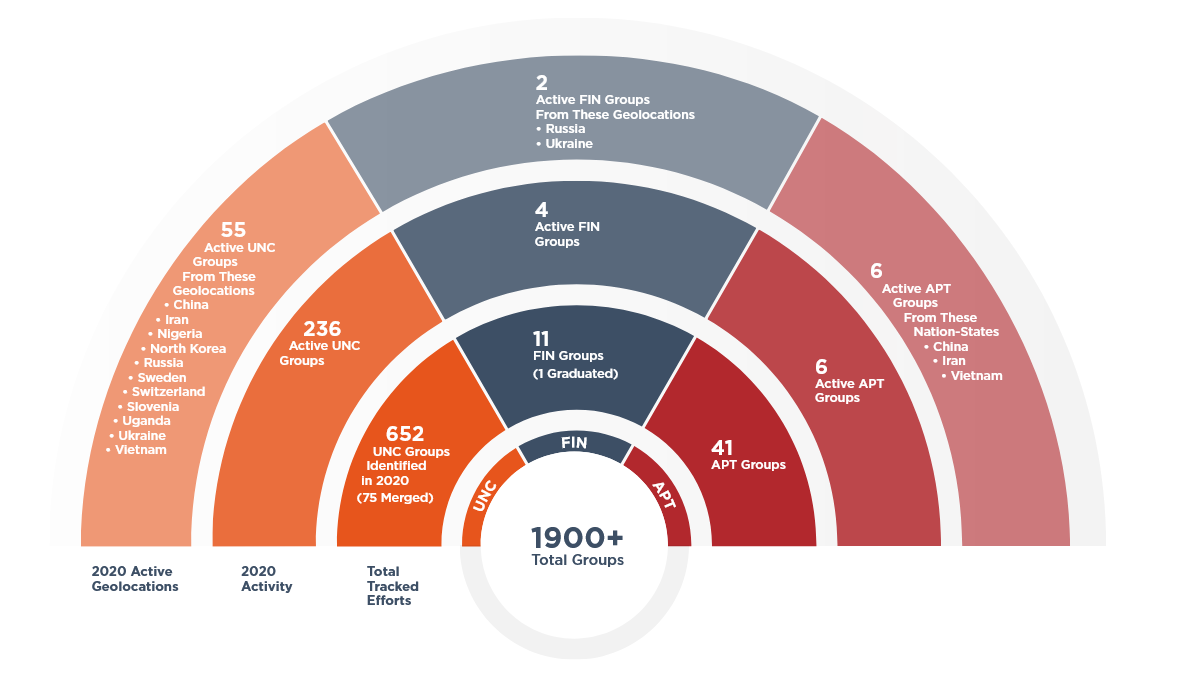
Among FireEye’s 1,900 known hacker groups, there are both “government” hackers (APT) and financially motivated groups (FIN), as well as unclassified groups (UNC, when it is not enough information to place them in one of the first two categories.
Analysts write that a total of 514 new malware samples were used by cybercriminals in 2020.
“Over the past year, hackers have created more than 500 new families of malware, which is in line with the previous year. This malware is divided into five main categories: backdoors (36%), downloaders (16%), droppers (8%), launchers (7%), and ransomware (5%)”, — say FireEye experts.
Approximately 19% of the total number of malware samples were publicly available, and 81% were either developed by private individuals or their availability was severely limited.
The most common threats are called the Beacon backdoor, which is included in Cobalt Strike, the Empire post-exploitation framework, the Maze and Netwalker ransomware, and the Metasploit pentester solution. That is, three out of five threats are in fact not malware, but completely legitimate information security tools (Beacon, Empire, and Metasploit) that cybercriminals simply prefer to use.
Other 2020 trends highlighted by FireEye:
- 59% of the security incidents investigated by Mandiant last year were initially detected by the organizations themselves, an improvement of 12% from the previous year.
- Ransomware has evolved into multifaceted extortion where actors not only deploy ransomware encryptors across victim environments, but also employ a variety of other extortion tactics to coerce victims into complying with demands.
- Pervasive ransomware campaigns drove down the median dwell time as threat actors sought to capitalize on shifting trends in the workspace and a global crisis.
- Threat actors took advantage of infrastructure supporting work-at-home with an increased focus on vulnerability exploitation.
Let me also remind you of the dramatic moment at the end of the last year, when Government hackers attacked FireEye, the largest provider of information security solutions.












