Security vendor FireEye and US authorities hit by SUNBURST malware attack
Last weekend, Reuters, the Washington Post and the Wall Street Journal reported that FireEye and the US authorities were hit by a government hacker attack on SolarWinds’ supply chain.
According to media reports, as a result of this operation were compromised the US Treasury Department and the National Information and Telecommunications Administration under the US Department of Commerce.
Shortly after these publications, representatives of the FireEye company released their own report on the incident.
According to the researchers, the attackers hacked into the software provider SolarWinds and then provided the Orion product with a malicious update. Due to the compromise suffered FireEye, as we already wrote about last week.
The compromise of SolarWinds was also confirmed by Microsoft analysts, who have already sent their customers a warning and a list of countermeasures to take in the case of a compromise.
The Washington Post cites its own sources, according to which many other government agencies in the United States were affected by the malicious version of Orion.
“The incident was deemed so serious that an emergency meeting of the US National Security Council was called at the White House over the weekend”, – reports agency Reuters.
Sources of the Washington Post link this attack to the Russian-speaking hack group APT29 (aka Cozy Bear and Dukes), which, according to experts, operates under the auspices of the Russian authorities.
FireEye experts do not write anything about APT29 and possible attribution; instead, the company assigned the group a neutral codename UNC2452. Moreover, the company believes that this attack was not aimed specifically at the United States:
“This campaign is widespread and affects public and private organizations around the world. The victims included government, consulting, technology, telecommunications and mining companies in North America, Europe, Asia and the Middle East. We expect that in the future there will be information about other victims in other countries and sectors of the world”, – write FireEye analysts.
SolarWinds representatives have already published a press release yesterday admitting the hacking of the Orion platform, designed for centralized monitoring and control. Typically, Orion is used in large networks to track all IT resources such as servers, workstations, mobile phones and IoT devices.
It is currently confirmed that versions 2019.4-2020.2.1 that were released between March 2020 and June 2020 were infected with malware. On December 15, 20202, the developers plan to release the 2020.2.1 HF 2 update, which is intended to “replace the compromised component.”
FireEye has named the detected malware SUNBURST and has already published a detailed technical report, along with rules for its detection.
Microsoft called the malware Solorigate, and Defender has already received the appropriate updates.
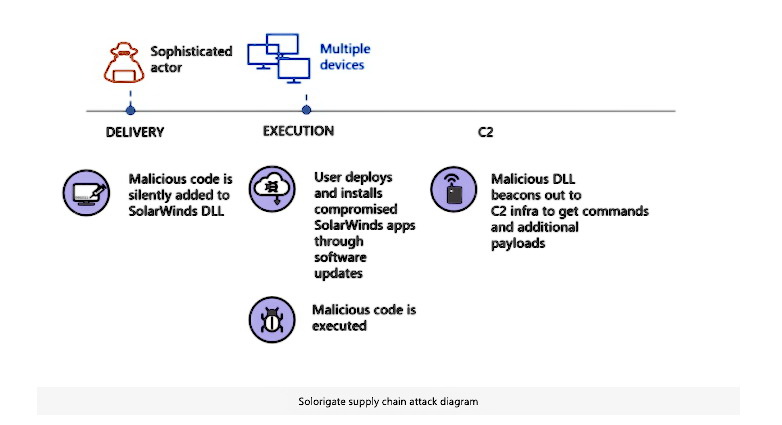
Experts from the Department of Homeland Security’s, Cybersecurity and Infrastructure Security Agency (DHS CISA) have already prepared their own instructions for government agencies so that they can detect and study systems compromised with the help of SUNBURST.
Let me remind you that we talked about how Chinese hackers use McAfee antivirus for spreading the malware.