Ransomware Facts, Trends & Statistics for 2020
2020 is very saturated with different events. It forced people to computerize their activity in all parts of the lifecycle. But the increased use of computers led to increased malware activity. The more people use their PCs – the bigger the chance of successful malware injection. And what about the most specific type of malware – ransomware?
Quick reference
Ransomware is a type of malware that injects in your PC and encrypts your files. After the encryption process, you will see the money ransom notes in every folder which contains encrypted files. An encryption algorithm that is used by ransomware may be different, but one of the most popular is AES-256. That algorithm supposes that there are 2^256 variants of passwords (78-digit number), so it is likely impossible to decrypt this cipher.
But some of the ransomware types are able to create the offline keys that are much easier to find. The peculiarity is that the single offline key may be used for several encryption cases. Hence, it is possible to use one offline key multiple times. That is why these keys are one of the main targets of anti-malware software developers: the more keys they would collect – the more ransomware cases their antivirus program will be able to decrypt.
So what?
Common statistics
One of the most popular objects for a ransomware attack are corporations. More computers equal to more possible ransomware cases, and, after that, more cash may be collected from one victim. We can see the following statistics for the corporations:
- Almost 75% of all ransomware attacks led to data encryption
- A little bit more than 25% of ransomware victims paid the ransom for data decryption
- Almost all (about 95%) of attacked corporations got their data back
- The total price that has been paid by companies who paid to ransomware distributors for decryption is about two times higher than the price of idle for the companies who get their data back without payments ($1,448,458 vs. $732,520)
As we can see, the total damage dealt by ransomware is more than $2 million. And no one knows where these funds were directed, because all payments are made in cryptocurrencies (most often – Bitcoin). The common thesis that this money may be used for terrorism-sponsoring or bribery funding at different levels. But, nonetheless, all this money is stolen, and the robbers must be found and imprisoned.
What was it?
Let’s check the most popular types of ransomware, which were relevant in the first half of 2020. Eight popular ransomware families were active. Here they are:
Such_Crypt ransomware
Such_Crypt ransomware is one of the newest ransomware. It appeared at the beginning of June, so it is not as spread and known as it could be. Ransomware uses AES256+RSA2048 encryption algorithm, so there is no chance to decrypt it without a proper tool, which has been created exactly for Such_Crypt. We got the information about only two ransomware of this family, which are known by its “extensions” – .mwahahah and .suchcrypt. These extensions are added to the original file name after the encryption process.
Snake ransomware
Snake ransomware is also a newbie among active ransomware. It was first noticed in January, and its cases are not numerous but very hard to solve. This ransomware looks like a targeted malware, which has already been used against several large corporations. Such targeting is going to be a trend for all the latest ransomware. The peculiarity of Snake ransomware is in its encryption behavior: every encryption case is launched separately, encryption process takes much more time than with other ransomware, and its own code is extremely obfuscated (much more than code of other ransomware). After the encryption, it changes the file extension, adding 5 random symbols to its default extension (i.e. document4.docx will be changed to document4.docxyAh6, table2.xlsx – table2.xlsxwYp2M).

STOP/Djvu ransomware
STOP/Djvu ransomware is one of the most widespread ransomware families. It is active since early 2019 and became extremely widespread in the fall of 2019. In October 2019, 73% of ransomware cases were of STOP/Djvu ransomware with more than 1500 submissions reported per day. Nowadays, the statistic shows the decrease by numbers – about 1000 cases per day, but its share in total ransomware cases still about 65-70% (and we are talking about reported cases only).
The reason for such STOP/Djvu popularity is its targeting on individuals and plenty of small companies, which have neither corporate security nor important data, but all their accounting is done through the PC.
The typical STOP/Djvu ransomware case can be noticed by plenty of readme.txt files in every folder, and by the specific ransomware extensions, which usually consists of 4-7 symbols.
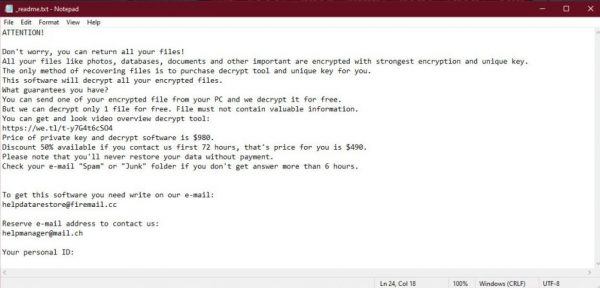
In contrast to other ransomware, STOP/Djvu family contains the information about the sum in the mentioned readme.txt file. The average invoice for file decryption varies from $450 up to $1000.
DCRTR ransomware
DCRTR ransomware is not a newbie, but quite a rare ransomware. The feature of this ransomware is that it specifies the e-mail which is supposed to be contacted for the decryption. The modified file extension looks like “[decryptor@cock.li].dcrtr”, with possible modification due to different ransomware variants. Several DCRTR-like ransomware doesn’t add the e-mail address to encrypted files extension, that is why they can be misrecognized as STOP/Djvu ransomware.
Because of its rarity, the encryption mechanism of this ransomware is not researched. No one can surely say if this malware uses symmetric or asymmetric cryptography. The average sum required for the decryption is $500-$1000 in cryptocurrencies. The versions without the e-mail in file extension names usually ask for the bigger sum.
Sfile ransomware
Another ransomware that is oriented exclusively on corporations. The usual way of injection is network security breaches so, in case of successful penetration, all computers in the network will be contaminated. Nonetheless, this ransomware places notes of ransom on every infected PC. Nowadays, the most active ransomware of this family is ESCAL; the specific extensions are .ESCAL-p9yqoly.
The RansomWare and Binary code, RansomWare Concept Security, and Malware attack.
Sfile ransomware has its own feature: it doesn’t hide that it removes your backups and cloud copies of your files, openly saying about it in money ransom note (named !!_FILES_ENCRYPTED_.txt). Ransomware distributors also placed a gibe in this file, saying something like “nothing personal, just business”
Dharma ransomware
Drahma is one of the oldest players among ransomware. Its activity was first spotted in late 2016, but it didn’t become massive. Possibly, the reason is on its distribution model: the majority of Drahma injection cases were done through the remote desktop protocol (RDP), which is not widespread through individuals. Yes, corporations are the often users of remote desktops, but, as statistic says, this popularity is not enough for successful Drahma spreading.

In the last 6 months, there were two new active versions of Drahma ransomware: PGP and HACK. Both of them like all other ransomware of this family uses asymmetric cryptography. These versions have quite a short ransom note (named README.txt), but earlier Drahma versions can have no ransom notes at all – just the e-mail in its specific extension like mentioned DCRTR ransomware. Like a lot of other ransomware families, this one also doesn’t specify any ransom sum in README.txt file.
Makop ransomware
This ransomware family is relatively large (30 known members), but not popular. Reasons are unknown: this ransomware usually distributes in the same way as STOP/Djvu, and also oriented on individuals. It’s “extension” also similar to other ransomware: it contains the e-mail addresses, which are supposed to be contacted for decryption and payment. But the peculiar thing is that these extensions can contain different e-mail and the same extension at the end (i.e. [savedata2@protonmail.com].makop”, “.[ruthlessencry@qq.com].makop”, “.[irisaneby@aol.com].makop” and so on.) Nonetheless, besides we have talked about before, this ransomware has two unique elements.
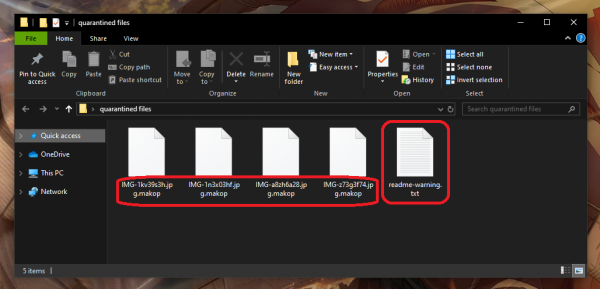
The first one is its ransom note. It is styled as a “questions&answers”, and consists of the answers for the most popular users’ questions (of course, in the manner that is more profitable for ransomware distributors). The second one is its “extensions”: they can be standard (.makop), as well as a bundle of symbols (i.e. [savedata2@protonmail.com].En3pUx).
And what is about conclusions?
As you can see, the ransomware activity became much bigger this year. The main reason for this is the coronavirus impact, which forсed to move all businesses online, away from crowds and contacts.
How to avoid the ransomware attack? Do not open dubious sites, untrusted links from unknown e-mails, do not use torrent-trackers, and try not to use cracked software. All mentioned actions/places are the most popular sources of ransomware, because of the absence of any control for the files contained inside.
Also, to get rid of the ransomware and all effects caused by it, use updated and licensed anti-malware software. Which anti-malware is better – Norton or McAfee, Bitdefender, or Malwarebytes – you can read on our site!












