Free Decryptor Arrived for MegaCortex Ransomware
Bitdefender has released a decryptor for files affected by MegaCortex ransomware attacks: the utility will allow victims of this group to recover their data for free.
The creation of this tool for decrypting infected files is the result of the joint work of Bitdefender experts, Europol analysts, the NoMoreRansom project, the Zurich prosecutor’s office and the Swiss cantonal police.
Let me remind you that we also said that Avast introduced free decryptors for AtomSilo, Babuk and LockFile ransomware, and also that During five years of operation, the No More Ransom project helped to save $900 million from ransomware.
Although experts have published a guide on how to use the tool, it works quite simply, as it is a standalone executable file that does not require installation and can automatically detect encrypted files on the system.
In addition, the decryptor can create backup copies of files in case something goes wrong during the decryption process and the files become damaged beyond repair.
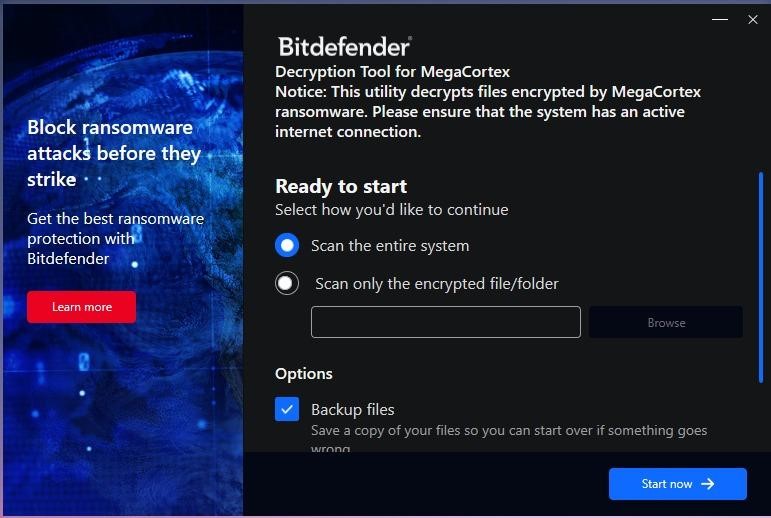
What’s more, for those who have previously tried to decrypt their files, the new tool offers advanced options to replace them with “clean” files.
Let me remind you that the MegaCortex ransomware was discovered back in 2019 and attacked mainly corporate networks, where it was found along with QBot, Emotet and Cobalt Strike beacons. Back then, cybersecurity experts wrote that MegaCortex operators were organizing targeted attacks, correlating the size of the ransom with the size of the victim companies.
During 2020, MegaCortex activity began to decrease and there were few victims affected by this ransomware. And in October 2021, Europol announced the arrest of 12 people responsible for 1,800 ransomware attacks in 71 countries around the world, many of which used MegaCortex and LockerGoga malware.
Previously, these arrests helped BitDefender create a free decryptor for victims, LockerGoga, as law enforcement officers were able to access the private master keys that were used to decrypt the victims’ keys.
Although BitDefender does not say how the private keys were obtained this time, the decryptor for MegaCortex was probably also created using the master keys found by the Zurich prosecutor’s office.











