MITER Security Advisory Exposed Data on Vulnerable Systems
The security advisories that MITER specialists publish for various CVEs contained links to remote administration consoles for a number of affected devices. Users accidentally noticed an error that has existed since April.
Journalists from Bleeping Computer report that a reader reported the problem to them, who was very surprised to find several references to vulnerable systems listed in the “references” section in the CVE bulletin.
Typically, this section provides links to primary sources (report, blog post, PoC demo) that explain the vulnerability. Sometimes security bulletins do include links confirming the existence of a vulnerability, but usually they lead to PoC or descriptions that explain the problem, but do not point to vulnerable systems.
Let me remind you that we also wrote that Vulnerability in Sophos Firewall Was Attacked Long Before Release of the Patch.
Journalists conducted their own investigation and tried to understand how this problem could have arisen at all. They say that an unnamed data disclosure vulnerability discovered in April contained links to a dozen active IoT devices vulnerable to the described bug.
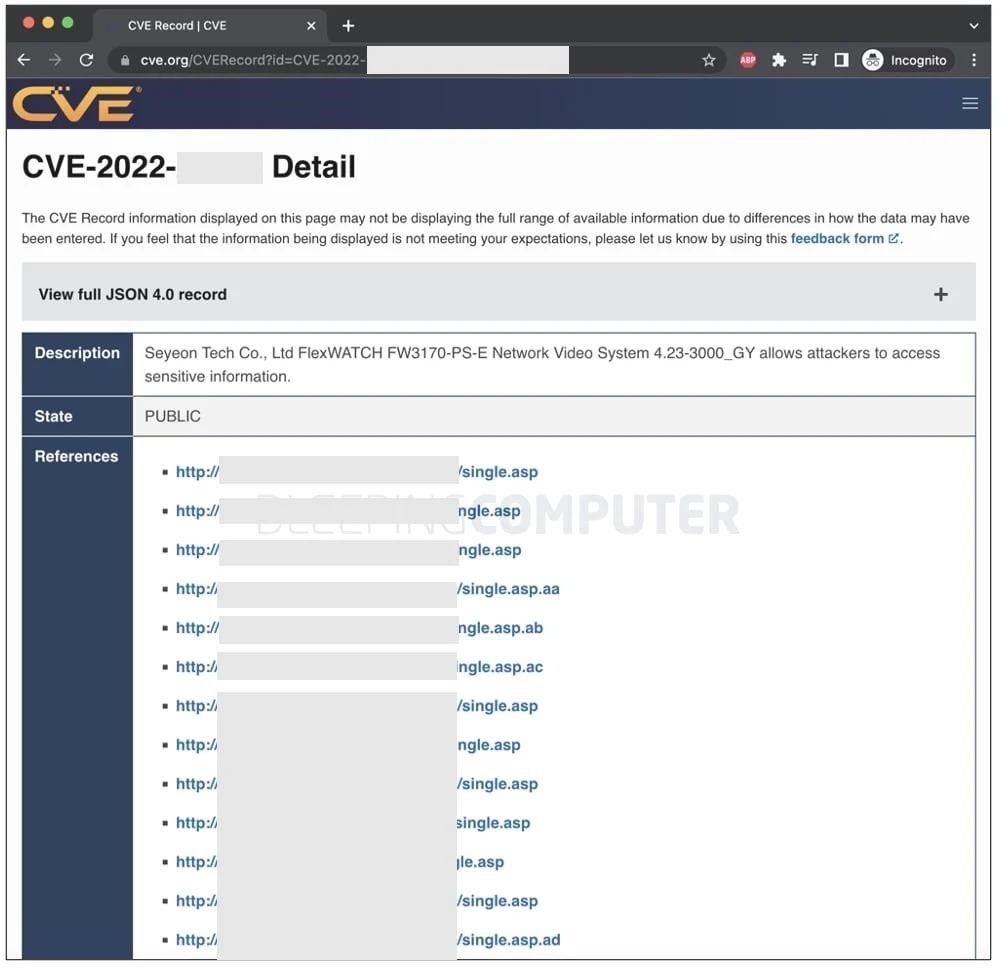
It is noted that many rely on MITER and NVD/NIST data for information about vulnerabilities, which means that links to vulnerable devices have spread across many open sources, vendors, CVE providers and so on.

Will Dormann
Interestingly, the representatives of MITER did not understand what the problem was and asked the journalists: “why these sites were not be included in the recommendations [on security]?”. The organization noted that in the past, MITER “often listed URLs or other hosts that could be vulnerable” in similar CVE bulletins.
Such a strange response from MITER prompted Bleeping Computer to contact security experts. Well-known information security researcher and CERT / CC analyst Will Dormann said that what happened was “abnormal and very BAD.”
As a result, the journalists independently found out that in this case, the article devoted to this vulnerability, published by Chinese researchers on GitHub, served as the primary source of what happened. At that time, the CVE for this vulnerability was “reserved” and was just pending review. It was this version of the bulletin that contained links to vulnerable devices cited as “examples”. That is, later this information was simply copied and pasted into the MITER bulletin. What’s more, that original GitHub post is now long since deleted.
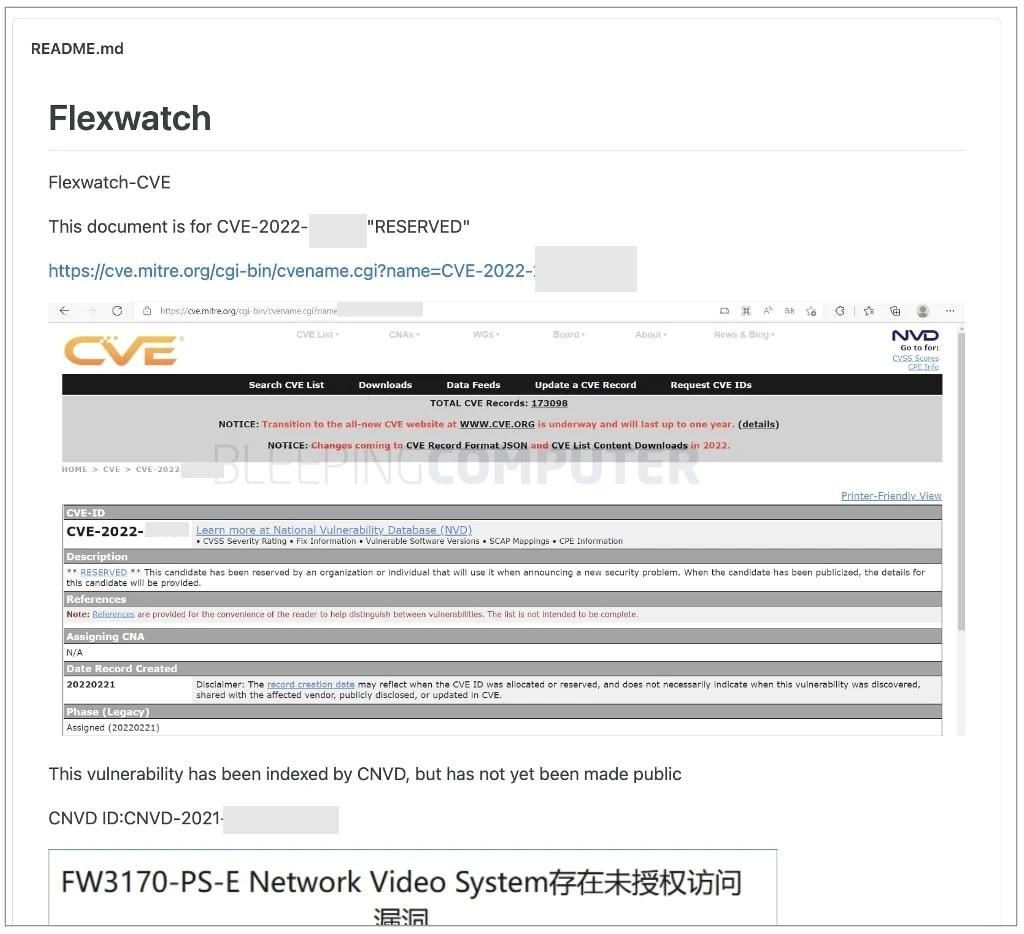
Will Dormann notes that the reason “I just copy-pasted someone else’s work” can hardly be regarded as an excuse, besides, such oversights clearly do not meet the MITER standards.
It is worth noting that a few hours after receiving a letter from journalists, MITER updated the problematic bulletin, removing all “helping” links from there that pointed to vulnerable devices.
At the same time, Bleeping Computer notes that this is not the first time that unverified links or “dead” URLs are found in the CVE MITER database. For example, 2031 mandriva[.]com URLs were recently found in 4530 CVE bulletins. Moreover, currently, these links are already “dead” and lead to an unsafe site with online casino advertising.












