Microsoft Defender Scanner for Log4j Problems finds non-existent bugs
The media reports that Microsoft Defender for Log4j problems is showing false warnings about some kind of “sensor hack” associated with the recently deployed Microsoft 365 Defender scanner for Log4j processes.
According to Bleeping Computer, such warnings mostly appear on Windows Server 2016 systems and says: “Microsoft Defender for Endpoint has detected possible sensor tampering with memory.” These warnings apply to the OpenHandleCollector.exe process.
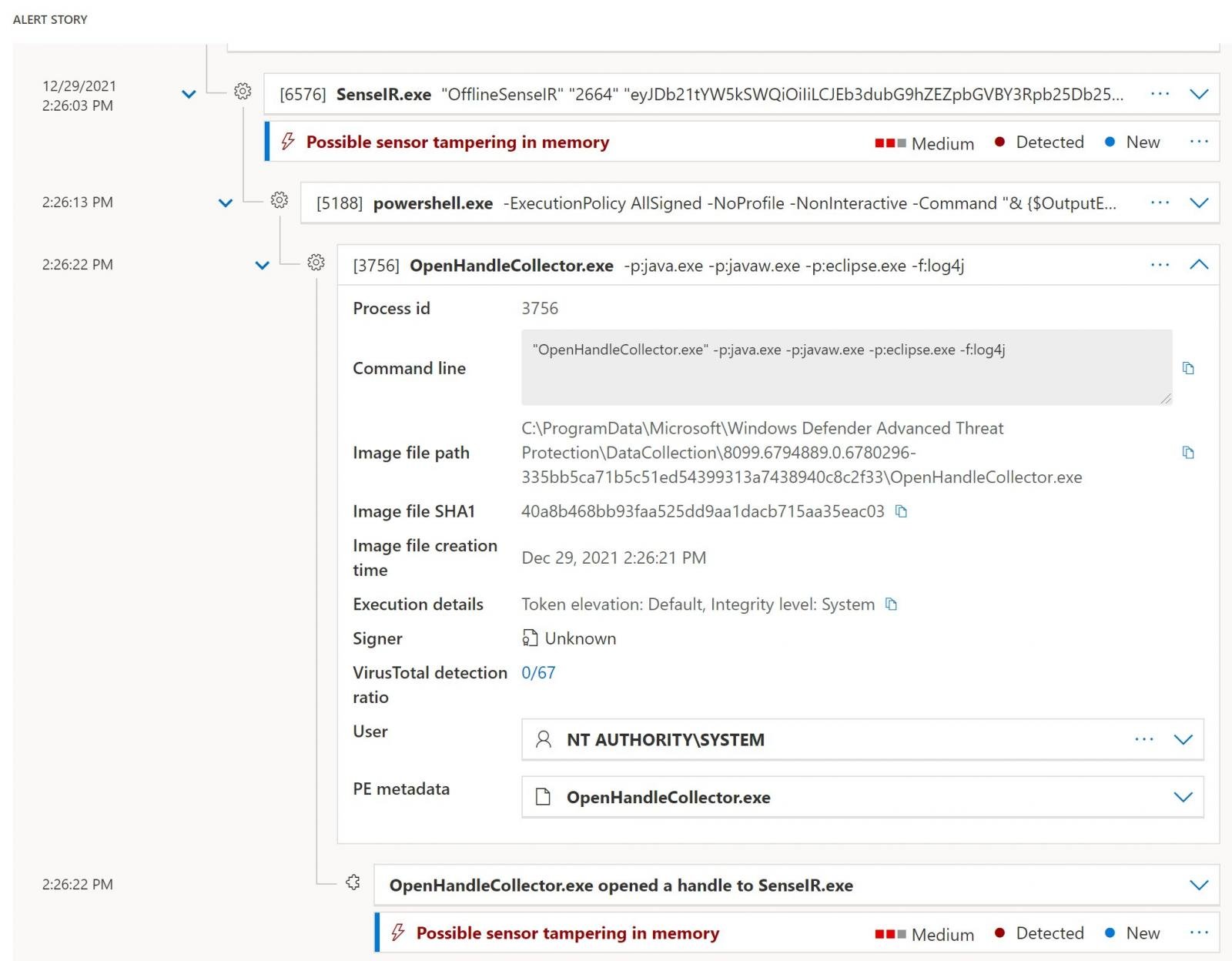
Microsoft representatives have already told outraged administrators that there is really nothing to worry about, as these are false positives. It is known that at the present time the company’s engineers are already studying the problem and are working on a patch, which should soon be released for all systems affected by the problem.
This newly launched Log4j scanner has been deployed with the new consolidated Log4j dashboard of Microsoft Defender 365 Threat and Vulnerability Management Portal, Microsoft said Tuesday.
The new dashboard is designed to help customers identify and remediate files, software, and devices that are susceptible to attacks that exploit Log4j vulnerabilities.
Journalists note that administrators are most likely already accustomed to the oddities in Microsoft Defender for Endpoint. After all, he previously marked Office documents as Emotet payloads, reported that network devices were infected with Cobalt Strike, and considered Chrome updates to be PHP backdoors.
Yes, and we noted the problems and features of this antivirus software, for example, we wrote that Microsoft Defender for Endpoint and Kaspersky doesn’t start after Windows update.
And also, for example, we wrote that Windows Defender creates thousands of files in Windows 10 due to bug.












