Vulnerability in Sophos Firewall Was Attacked Long Before Release of the Patch
Volexity experts talked about how hackers exploited a 0-day vulnerability in Sophos Firewall, which was fixed by the manufacturer in March 2022. Researchers say that Chinese hackers from the DriftingCloud group exploited the bug.
Let me remind you that in March 2022, a patch was released for the CVE-2022-1040 vulnerability, which was rated as critical on the CVSS scale (9.8 points out of 10 possible). At the time, it was reported that the bug allows remote attackers to bypass authentication through the firewall’s user portal or through the web admin panel and then execute an arbitrary code.
The vulnerability was originally discovered by an anonymous researcher who reported it through the official bug bounty program and stated that the issue affects Sophos Firewall 18.5 MR3 (18.5.3) and earlier.
At that time, attacks using this problem were already reported, but little was known: the manufacturer wrote that the bug was mainly exploited in attacks against targets from South Asian countries.
As Volexity analysts now say, the Chinese faction, which they track under the name DriftingCloud, has been using CVE-2022-1040 since early March, starting about three weeks before the release of the patch. The attackers used the exploit to compromise the firewall, install webshell backdoors and malware.
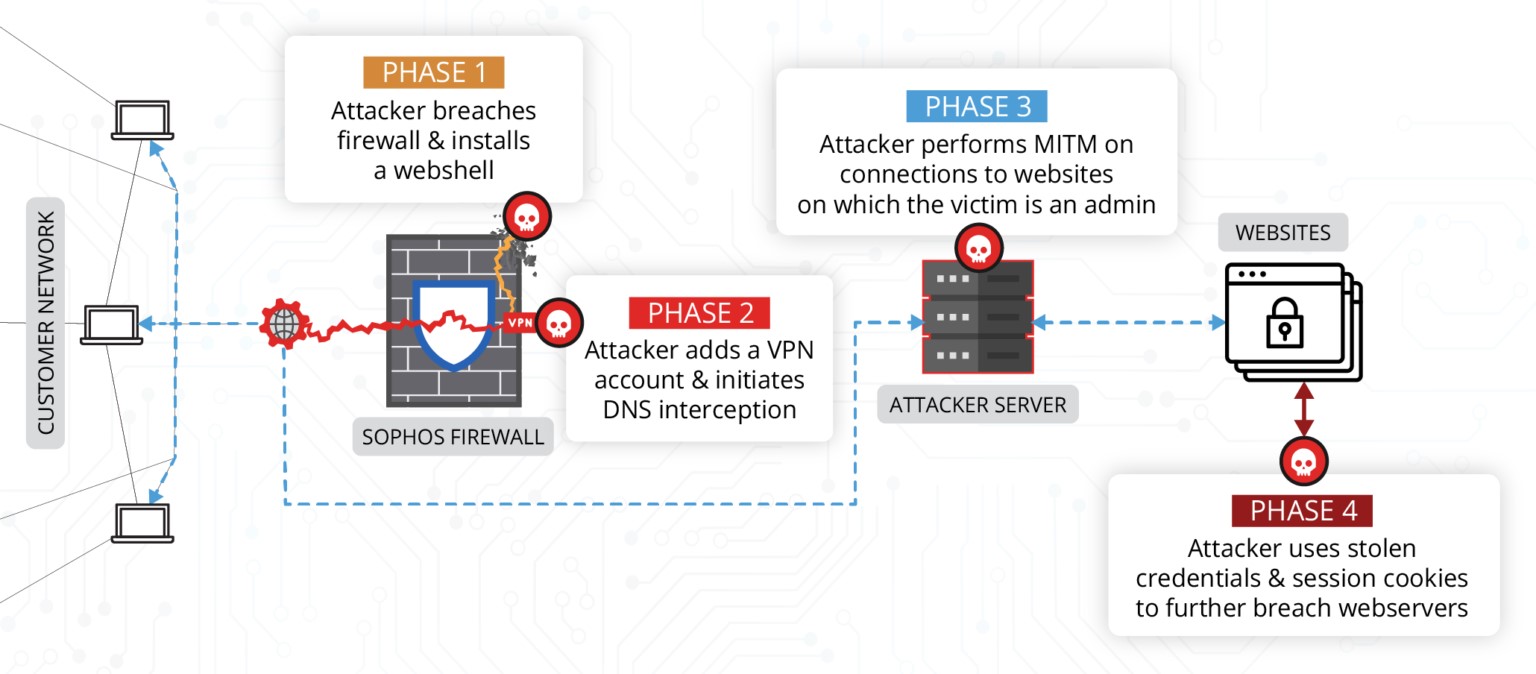
Gaining access to the Sophos Firewall was only the first stage of compromise before the MitM attack (by changing DNS responses for certain sites controlled by the victim company).
As a result, the hackers gained access to the administration pages of the CMS using stolen cookies and installed the File Manager plugin to process files on the site (upload, download, delete, edit). Also, after gaining access to the web server, the attackers installed PupyRAT, Pantegana, and Sliver, three widely available remote access malware.
When Volexity began investigating these hacks, the attackers were still active, enabling investigators to follow almost all stages of the attacks. It is noted that hackers sought to mask their traffic by gaining access to the installed web shell through requests to the legitimate login.jsp file.
It is also noted that during the attacks, the hackers used the Behinder infrastructure, which was previously used in attacks by other Chinese APTs that exploited the CVE-2022-26134 problem in Atlassian Confluence.