Microsoft Defender ATP has mistakenly detected Mimikatz and Cobalt Strike on users’ machines
Many sysadmins have had extremely nervous days this week: Microsoft Defender ATP (Advanced Threat Protection) corporate solution mistakenly detected Mimikatz and Cobalt Strike infections on devices and issued false warnings.
[dropcap]L[/dropcap]et me remind you that hackers, from government APT groups to ransomware operators, for a long time beloved the legitimate commercial framework Cobalt Strike, created for pentesters and the red team and focused on exploitation and post-exploitation.Although it is not available to ordinary users and the full version is priced at about $3,500 per install, attackers still find ways to use it (for example, relying on old, pirated, jailbroken and unregistered versions).
Typically, attackers use hacked versions of Cobalt Strike to gain stable remote access to compromised networks and use them during ransomware attacks.
In turn, Mimikatz is a post-exploitation tool designed to collect passwords from compromised systems. It is commonly used by many “commercial” hack groups as well as government hackers.
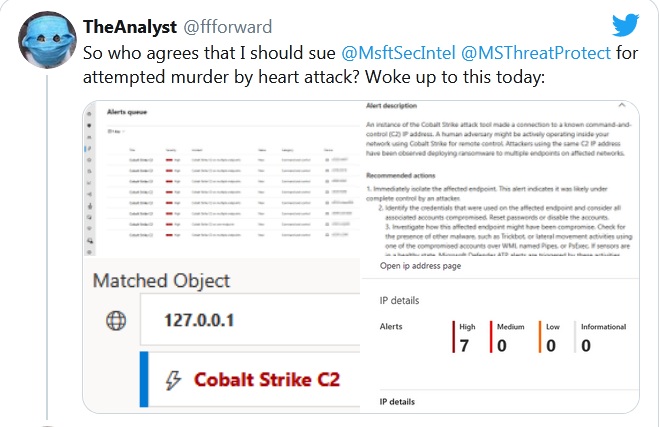
Although the administrators definitely had more grey hair after the accident, it soon became clear that the infection reports were just false positives of ATP in Microsoft Defender, since it considered network connections to 127.0.0.1 (localhost) to be traffic from Cobalt Strike C&C servers.
The problem of false positives has already been confirmed on Twitter by Microsoft Threat Intelligence analyst Kevin Beaumont. The expert writes that now such alarms should be marked as false in the logs. The incorrect signature that caused this issue has also been fixed.
“We’ve addressed the issue that led to false positive alerts and corrected notifications some customers may have received”, — told SecurityWeek magazine a Microsoft spokesperson.
However, John Hensinski, director of security at cybersecurity company Expel and one of the people who followed the incident, advised organizations not to immediately dismiss Cobalt Strike warnings in Defender ATP, but instead follow their triage process as normal.
Let me remind you that about earlier news that Windows Defender recognizes CCleaner as PUA.












