LockBit Ransomware Uses Windows Defender to Download Cobalt Strike
LockBit 3.0 ransomware operators abuse the Windows Defender command line tool to download Cobalt Strike beacons on compromised machines and avoid detection.
It is worth recalling that Cobalt Strike is a legitimate commercial tool designed for pentesters and the red team and focused on exploitation and post-exploitation.
Unfortunately, it has long been loved by hackers ranging from government APT groups to ransomware operators. Although Cobalt Strike is quite expensive and inaccessible to ordinary users, attackers still find ways to use it (for example, rely on old, pirated and hacked versions).
Let me remind you that we also reported that Zloader Trojan Disables Microsoft Defender on Victims’ Systems.
Sentinel Labs experts say that attackers have now begun to abuse the Microsoft Defender command-line tool, MpCmdRun.exe, to side-load malicious DLLs that decrypt and install Cobalt Strike beacons on the victim’s machine.
In general, side-loading Cobalt Strike beacons into compromised systems is not new to LockBit operators, as hackers have been using similar techniques based on the abuse of VMware command line utilities for quite some time.
The initial point of compromise, in both cases studied by Sentinel Labs analysts, was the exploitation of a Log4j vulnerability on the affected VMWare Horizon servers, which led to the launch of PowerShell code. Once they have access to the target system and the required privileges, the attackers use PowerShell to download three files: a clean copy of the Windows CL utility, a DLL file, and a LOG file.
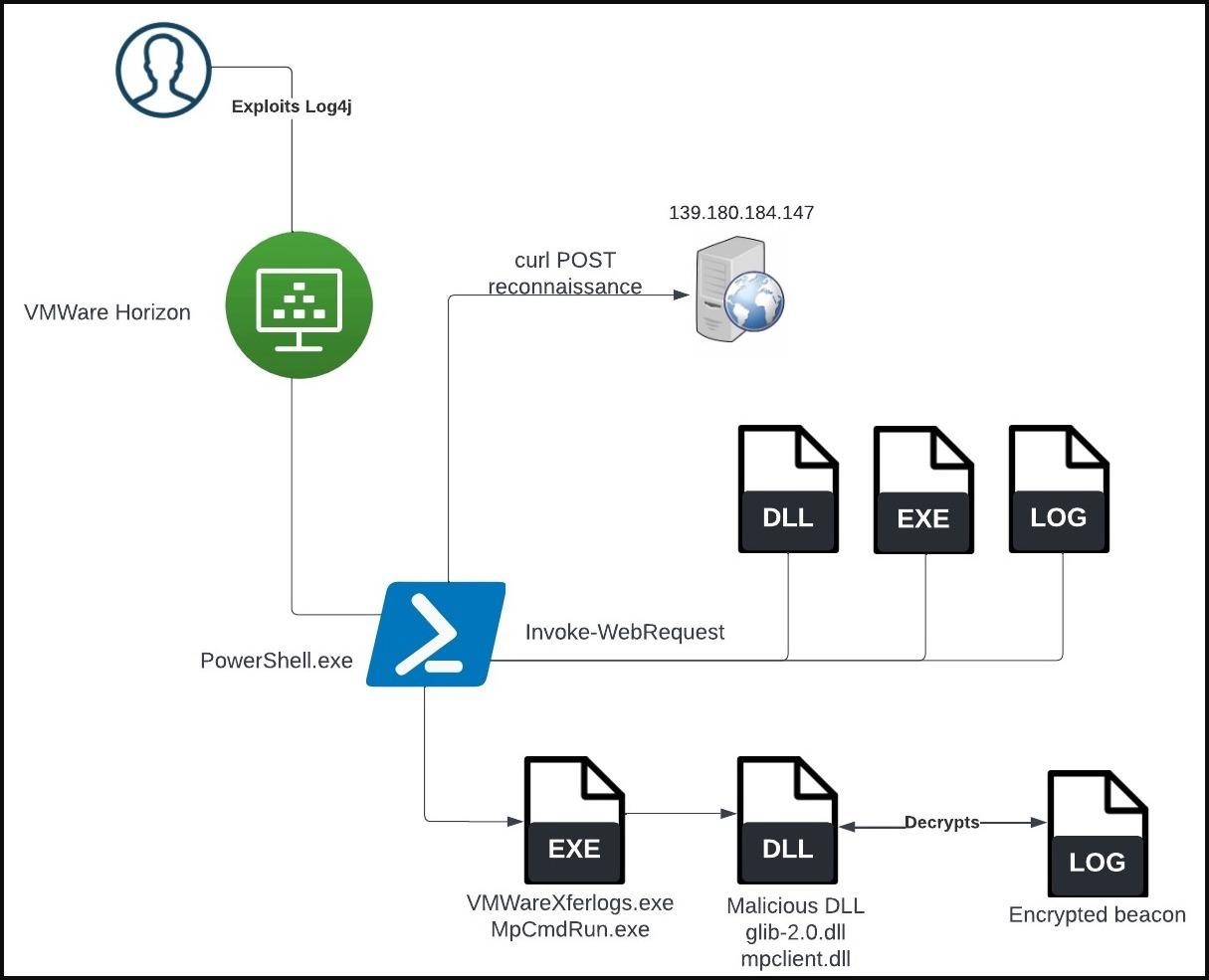
MpCmdRun.exe is a command-line utility for running Microsoft Defender tasks that supports commands to scan for malware, gather information, repair items, perform diagnostic tracing, and more.
Usually, when MpCmdRun.exe is executed, it loads a legitimate DLL (mpclient.dll), which is necessary for the program to work correctly. In the case studied by Sentinel Labs, the attackers created their own malicious version of mpclient.dll and placed the file in a location that would be given priority when loaded.
When the attacker’s code is executed, the encrypted Cobalt Strike payload is loaded and decrypted from the c0000015.log file created at an early stage of the attack.
Analysts write that it is not yet clear why one of LockBit’s campaigns relies on Windows Defender instead of VMware’s usual abuse to download Cobalt Strike beacons. This is likely due to bypassing some targeted protections that were implemented in response to past hacker tactics.












