The Researcher Managed to Turn Antiviruses and EDR into Wipers
A specialist from SafeBreach has figured out how to turn the popular EDR (endpoint detection and response) and Microsoft, SentinelOne, TrendMicro, Avast and AVG antiviruses into wipers. To do this, the expert used the data deletion functionality built into security products.
Or Yair of SafeBreach writes that attackers can exploit the security solutions already in the target system for their destructive attacks.
Let me remind you that we also said about Critical Bug in VMware Products, and also that PoC Exploit for Critical Vulnerability in Fortinet Products Appeared.

Or Yair
This will make attacks stealthier, and hackers won’t have to gain elevated privileges on victim systems. Also, abusing EDR and antivirus to destroy data is a good way to bypass protections, since the ability to delete files in such products is common and is unlikely to attract attention.
Antiviruses and EDR constantly scan the computer’s file system for malicious files, and if they are found, they try to quarantine or delete them. In addition, with real-time protection enabled, the file is automatically scanned upon creation to determine if it is malicious, and if so, it is deleted or quarantined.
Yair’s idea was to create a folder called C:\temp\Windows\System32\drivers and store Mimikatz as ndis.sys in it. Since Mimikatz is detected by most EDR platforms, including Microsoft Defender, it was planned that the file would be marked as malicious when it was created. But before EDR could delete the file, the researcher was going to quickly delete the C:\Temp folder and create a junction from C:\Temp to C:\Windows. Yair believed that in this case EDR would try to delete the legitimate ndis.sys file located in C:\Windows\system32\drivers\ndis.sys.
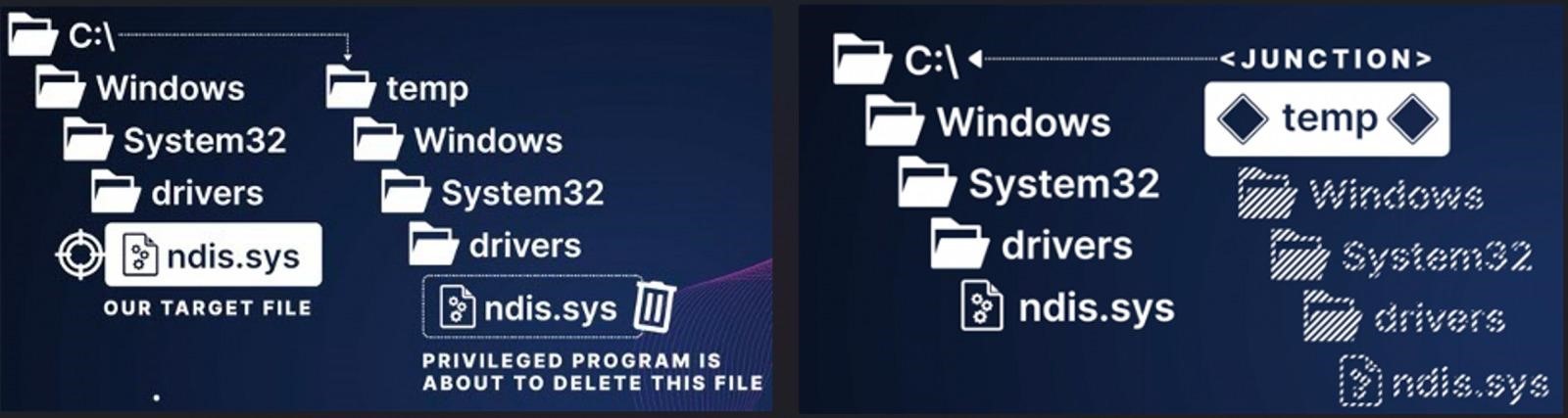
However, this approach didn’t work because some EDRs prevented further access to the file, including deletion, if it turned out to be malicious. In other cases, EDR detected the deletion of a malicious file, and therefore the software canceled the pending file erasure altogether.
Then Yair decided that it was possible to create a malicious file, keep its handle, leaving it open, and not determine which processes were allowed to write / delete it, so that EDR and antiviruses that detected the file could not erase it. In this case (after detecting the malware and not having the rights to delete the malicious file), the security tools suggested that the researcher approve a system reboot that would release the handle, after which the malicious file would become available for deletion.
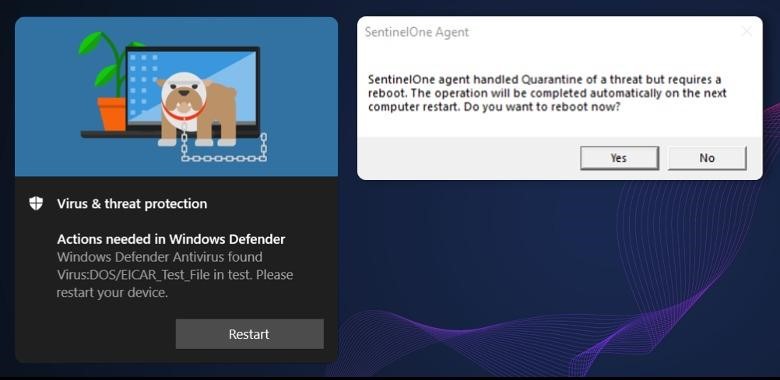
The command to delete the file in this case is written to the registry (PendingFileRenameOperations), which actually led to its deletion during the reboot. At the same time, Windows deleted the files “blindly”, following the junction. The expert notes that this method is also effective for bypassing the Controlled Folder Access functionality, which is usually used to protect against ransomware. Such protection will not prevent EDR and antiviruses from deleting user files.
As a result, the researcher created an exploit-wiper, which was named Aikido Wiper. Yair writes that it is undetectable, can be run by unprivileged users to delete data in directories of administrator users, and in the end is capable of making the system unbootable.
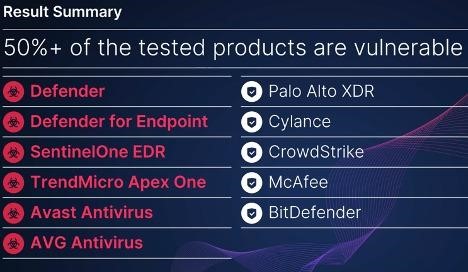
Yair tested his viper against 11 security products and found that Microsoft Defender, Defender for Endpoint, SentinelOne EDR, TrendMicro Apex One, Avast Antivirus and AVG Antivirus are vulnerable to such an attack. Failed to fool Palo Alto, Cylance, CrowdStrike, McAfee and BitDefender solutions.
In Aikido Wiper, the expert used exploits for vulnerabilities in Microsoft Defender, Defender for Endpoint and SentinelOne EDR, since they were the easiest to implement in wiper. As a result, Yair notified all affected vendors of his findings (between July and August 2022), and by now they have all released patches.
The identified issues have been assigned the following IDs: CVE-2022-37971 (Microsoft), CVE-2022-45797 (Trend Micro), and CVE-2022-4173 (Avast and AVG).
As a result, the problems were fixed in the following versions of security products:
- Microsoft Malware Protection Engine – 1.1.19700.2 and newer;
- TrendMicro Apex One – Hotfix 23573 and Patch_b11136 and newer;
- Avast and AVG Antivirus – 22.10 and later.
We also recall that the media wrote that Azov Ransomware Wiper Operators Try to Set Up Ukraine and Well-Known Information Security Specialists.