Kaspersky Lab’s Amazon SES token was used for phishing
Kaspersky Lab reported that its legitimate Amazon Simple Email Service (SES) token, previously issued to a third-party contractor, was used by cybercriminals as part of a phishing campaign aimed at Office 365 users.
Amazon SES is a scalable email service that allows developers to send emails from any application, including marketing and bulk mailing.
Experts associate these phishing attacks with several criminal groups that used two cornerstones of phishing for the attacks: Iamtheboss and MIRCBOOT.
The attackers did not try to impersonate Kaspersky Lab, but disguised their messages as missed fax notifications, redirecting potential victims to phishing pages designed to collect their credentials.
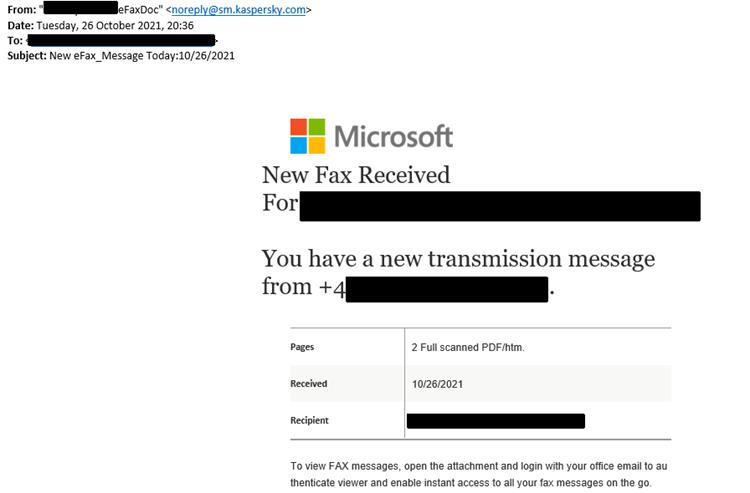
In doing so, the criminals used the official mail of Kaspersky Lab and sent letters from the Amazon Web Services infrastructure, which probably helped them to bypass most of the Secure Email Gateway (SEG) protections.
Kaspersky Lab encourages users that were affected by these targeted phishing attacks to exercise caution and remain vigilant even when prompted for their credentials or other confidential information, even if messages requesting such information come from familiar brands or email addresses.
Let me remind you that I also talked about, that Kaspersky Password Manager generated weak passwords due to a bug.










