Windows Defender considers the HOSTS file to be malicious if it blocks telemetry
Bleeping Computer reporters noticed that recently Windows 10 and Windows Defender consider the hosts file (C:\Windows\system32\driver\etc\hosts) to be malicious if it contains settings that block telemetry collection.
According to the publication, since the end of July, the modified hosts file has been identified as posing a threat “SettingsModifier: Win32/HostsFileHijack“. If the user clicks on “More” after receiving such a warning, nothing is explained to him, only he is told that the file exhibits “potentially unwanted behavior.”
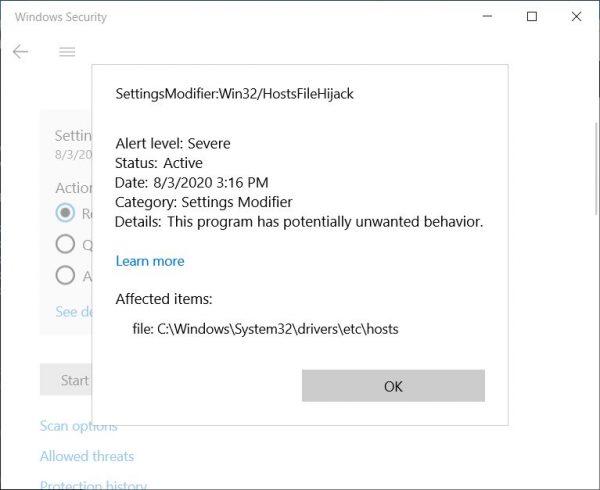
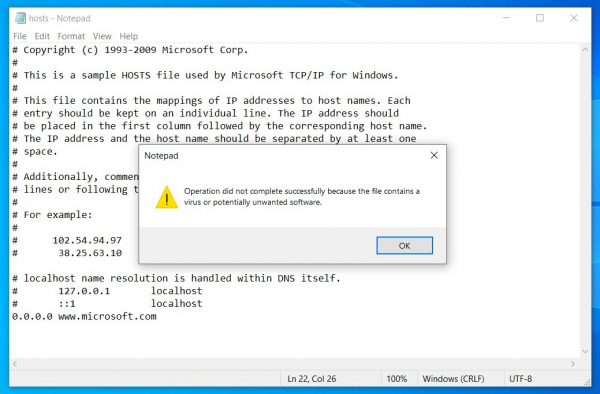
If the user agrees to eliminate the “threat”, the system will clear the hosts file and return it to its default state. It is also possible to ignore the problem, but this will allow any modifications to hosts in the future, including malicious ones.
Lawrence Abrams, Bleeping Computer founder, notes that overall the problem of false positives for the hosts file is not new, but in recent weeks people have suddenly started to massively complain about such warnings (1, 2, 3).
Abrams writes that he thought it was false positives again, but still runing several tests.
“As it turned out, it is enough to block the Microsoft servers collecting telemetry through the hosts file, and then the problems begin”, – says Lawrence Abrams.
In particular, problems arise when you try to block the following addresses:
- www.microsoft.com
- microsoft.com
- telemetry.microsoft.com
- wns.notify.windows.com.akadns.net
- v10-win.vortex.data.microsoft.com.akadns.net
- us.vortex-win.data.microsoft.com
- us-v10.events.data.microsoft.com
- urs.microsoft.com.nsatc.net
- watson.telemetry.microsoft.com
- watson.ppe.telemetry.microsoft.com
- vsgallery.com
- watson.live.com
- watson.microsoft.com
- telemetry.remoteapp.windowsazure.com
- telemetry.urs.microsoft.com
Because of this, the specialist came to the conclusion that Microsoft apparently recently updated Defender in such a way that it would detect if the company’s servers were added to the hosts file and the user is trying to block collection of telemetry.
Microsoft has not yet commented on the situation.
It looks like Windows Defender is behaving more and more aggressively (actually Microsoft developers, of course) – we recently wrote that Windows Defender recognizes CCleaner as PUA.