Search for Random Leaks of API Keys, Passwords and Tokens Earned for All GitHub Users
GitHub announced that a service for scanning public repositories for random leaks of sensitive data (API keys, account passwords, authentication tokens, and so on) is now available to all users and now it can search for forgotten secrets throughout the publication history.
Information security specialists also said that GitHub will remove exploits for vulnerabilities under attack.
Let me remind you that we also wrote that Samsung Message Guard Will Protect Galaxy Devices from Zero-Click Attacks, and also that OpenAI Introduced a Tool for Detecting Text Generated by Artificial Intelligence.
Since attackers actively search public repositories on GitHub for various secrets (and then use them to hack, steal data, or try to impersonate another company), GitHub began work last year on proactively protecting developers from accidental leaks.
At the time, it was announced that an additional security feature called push protection would allow organizations running GitHub Enterprise Cloud with a GitHub Advanced Security license to enable additional scanning for their repositories.
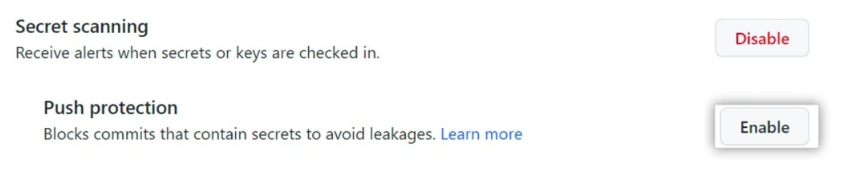
In essence, the new feature is intended to prevent accidental disclosure of data before committing code to remote repositories. The novelty is able to detect 69 types of tokens accidentally forgotten in the code, including API keys, authentication tokens, access tokens, management certificates, credentials, private keys, secret keys, and so on. It is emphasized that the defense relies only on “clearly identifiable patterns”.
Thus, if GitHub Enterprise Cloud finds a secret in the code before pushing it, git push is blocked so that the developer can review and remove the secrets from the code that was trying to commit. Also, developers will be able to mark such warnings as false, test, or leave them for later correction.
Since December 2022, the company has been beta testing the free secret scanning functionality, which searches for forgotten secrets in all public repositories and can detect over 200 token formats. Since then, the new feature has been included in 70,000 public repositories.
GitHub developers have now announced that the service is already available for free to all users, and all owners of public repositories can turn on secret scanning alerts to protect their data.










