Grouping LockBit Announced the Hacking of the Information Security Company Mandiant
On the website of the hack group LockBit, a message appeared in which hackers announced that Mandiant had been hacked and threatened to publish 356,841 files allegedly stolen from the information security company. It seems that the attackers did not like that in a recent study, Mandiant specialists linked their activities to the operations of Evil Corp.
Let me remind you that we also wrote that Attackers hacked cybersecurity company Qualys through Accellion FTA.
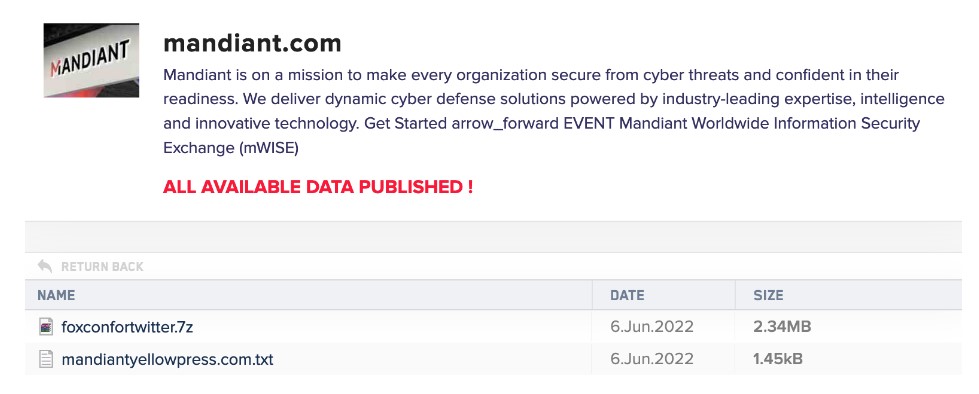
Bleeping Computer writes that LockBit did not report exactly which files were stolen from Mandiant systems, and the list of files on the leak page was empty. However, it showed a file named mandiantyellowpress.com.7z with a size of 0 bytes, which appeared to be associated with the domain mandiantyellowpress[.]com (registered yesterday). Visiting this page redirected to ninjaflex[.]com.
When the publication reached out to Mandiant for comment, the company said it was already investigating the incident, but so far found no signs of hacking.
Now that the “leak” has been made public, it has become clear that the hackers did not seem to have stolen anything, but are trying in a very original way to refute the recent Mandiant study, in which experts linked LockBit to the operations of Evil Corp.
Let me remind you that, according to experts, now Evil Corp is acting as one of the “partners” of LockBit, thus trying to evade US sanctions, as well as save resources and time to develop their own malware.
Apparently, LockBit fears loss of income and the fact that their victims will stop paying ransoms, since Evil Corp is under sanctions.
You might also be interested in our post on Mandiant M-Trends 2022: Companies significantly improved cyberthreat detection time.










