Emsisoft Says Hackers Are Spoofing Its Certificates
Experts from the information security company Emsisoft have warned that attackers are spoofing and using certificates for code signing, posing as Emsisoft. Attackers target a company’s customers using its products in the hope of bypassing their protection.
Let me remind you that we also wrote that Antivirus solution provider Emsisoft reported data leak, and we did a review: Emsisoft Anti-Malware Review 2022 – Is It Any Good?
Emsisoft says in its security bulletin that one of its customers was recently targeted by hackers who used an executable signed with a fake Emsisoft certificate.
Although the attack failed and Emsisoft software blocked the hackers’ file due to an invalid signature, the company warns customers to be vigilant against such attacks.
According to Emsisoft experts, the attackers probably gained initial access to the compromised client device using RDP brute force or used stolen credentials belonging to an employee of the attacked organization.
Once they gained access, the attackers attempted to install the legitimate open source MeshCentral application for remote access, which is usually trusted by security solutions. However, the MeshCentral executable in this case was signed with a fake Emsisoft certificate claiming to be issued by a “trusted Emsisoft Server network CA”.
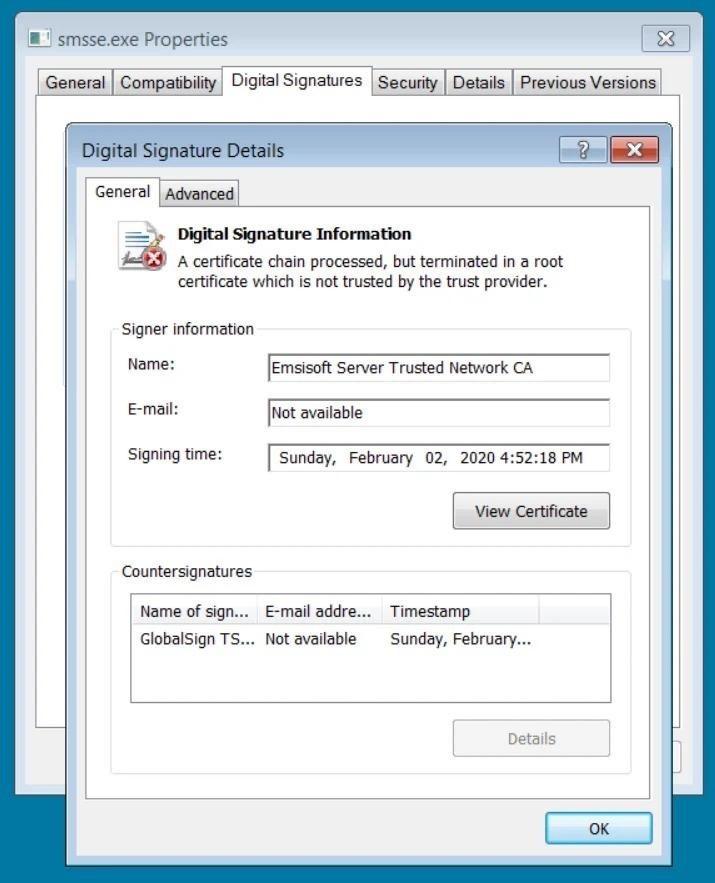
As a result, the Emsisoft software scanned the file, but marked it as “Unknown” due to an invalid signature and placed it in quarantine.
It is noted that if an employee of the target company perceived this warning as a false positive, he could allow the application to run, and attackers could gain full access to the device.
Let me also remind you that the media reported that Emsisoft Released a Free Tool to Decrypt Data Corrupted by AstraLocker and Yashma.











