Avast specialists discovered a fake version of Malwarebytes antivirus
Specialists of the software for protecting computer systems manufacturer Avast discovered a fake version of the Malwarebytes antivirus. A malicious version of Malwarebytes antivirus scanner secretly installs the Monero cryptocurrency miner.
[dropcap]Late[/dropcap] last week, Avast began detecting the distribution of fake installation files for the popular Malwarebytes antivirus scanner, which contained a backdoor. This backdoor downloaded on computers the Monero cryptocurrency miner, popular among hackers.A miner is a third-party program that is installed on a computer and “mines” cryptocurrency using the resources of the device. Hidden miners do this unnoticed by the user, bringing income to cybercriminals.
The most common name for the malicious file we detected is “MBSetup2.exe“. Most of the attack attempts were made in Eastern European countries.
“We have not yet identified the source of the virus, but we can confirm that it was not posted on the official Malwarebytes channels, which remain reliable download sources”, – write Avast experts.
The fake MBSetup2.exe installation file is an unsigned file that has been infected with malicious files Qt5Help.dll and Qt5WinExtras.dll with invalid digital signatures. All other portable executables contained in the installer are signed with valid Malwarebytes or Microsoft certificates.
“We have notified Malwarebytes about the distribution of fake installation files for their program. You can familiarize yourself with the hash of malicious files by this link”, – said Avast experts.
The authors of this downloader can change its content at any time, thereby spreading other malicious programs to infected devices.
After launching the file, appears the installation wizard of the fake Malwarebytes. The malware installs fake Malwarebytes in the %ProgramFiles(x86)%\Malwarebytes folder and hides most of the malicious payload inside one of two DLL files, Qt5Help.dll. The installer then notifies victims of the allegedly successful installation of Malwarebytes.
The malware then installs itself as a service called “MBAMSvc” and downloads a Monero cryptocurrency miner called Bitminer, which is powered by another miner, XMRig.
The installation wizard was created using the Inno Setup system. It differs from the original Malwarebytes installer.
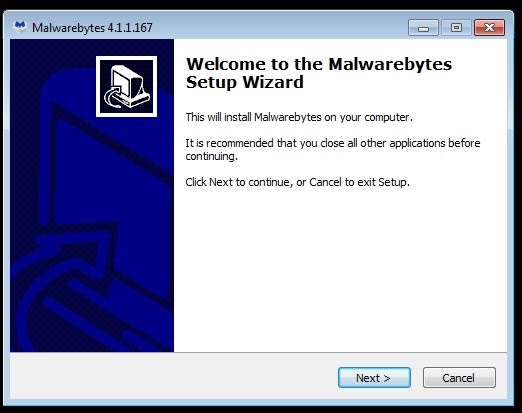
Installation window of the fake file
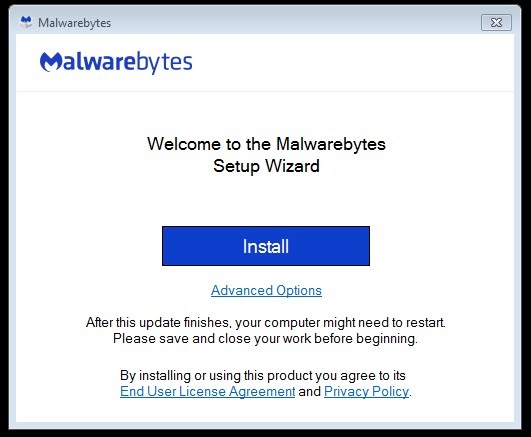
Original program installation window
How to check if your computer is infected?
In case you have recently installed programs from Malwarebytes, you can make sure they are safe by searching for one of the following files on your device^^^:
- %ProgramData%\VMware\VMware Tools\vmtoolsd.exe
- %ProgramData%\VMware\VMware Tools\vmmem.exe
- %ProgramData%\VMware\VMware Tools\vm3dservice.exe
- %ProgramData%\VMware\VMware Tools\vmwarehostopen.exe
If any of these files are present, all files in the %ProgramFiles(x86)%\Malwarebytes folder and executables in the %ProgramData%\VMware\VMware Tools\ folder should be removed.
It is also recommended to remove the MBAMSvc service.
“Avast Antivirus detects and quarantines malicious installation and DLL files, making MBAMSvc safe”, – expectedly offer Avast employees ))).
You can also uninstall the service by opening a command prompt with administrator rights and executing the “sc.exe remove MBAMSvc” command.
Read our 2020 real-life Malwarebytes product review, by the way, and compare Malwarebytes vs Bitdefender.












