Experts Found Long-Standing Bugs in Avast and AVG Antiviruses
SentinelOne specialists found bugs in Avast and AVG antiviruses related to their common anti-rootkit protection driver (aswArPot.sys). Vulnerabilities appeared in the code with the release of Avast 12.1, back in 2012, and all this time remained unnoticed.
Let me remind you that we also reported that Chinese hackers use McAfee antivirus for spreading the malware, and that ESET fixed a serious vulnerability in its products for Windows.
Bugs in Avast and AVG antiviruses were discovered in December 2021, received the identifiers CVE-2022-26522 and CVE-2022-26523, and affect Avast and AVG antiviruses. Since Avast acquired AVG in 2016, the problems appeared to be related to the generic anti-rootkit protection driver. Currently, the vulnerabilities have already been fixed: they were addressed back in February 2022 with the release of version 22.1.
SentinelOne said the vulnerabilities were assessed as “severe” because they allowed an attacker with limited privileges on the system to execute code in kernel mode and eventually take full control of the device.
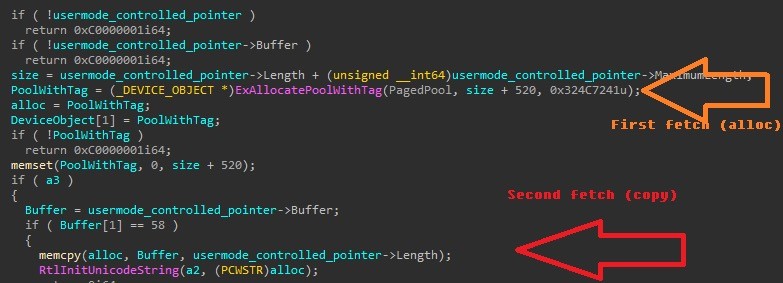
Experts have no evidence that hackers abused these vulnerabilities, but it is noteworthy that the information about the bugs was published just a few days after Trend Micro detailed the AvosLocker malware, which used a different problem in its attacks in the same driver to disable anti-virus products.












