Mandiant M-Trends 2022: Companies significantly improved cyberthreat detection time
The time that attackers go undetected on a victim’s network was declining for the fourth year in a row, according to the Mandiant M-Trends 2022 report.
Cyberthreat detection time has been reduced to 21 days in 2021 compared to 24 days in 2020. Ransomware was detected on average within five days, while other attacks went undetected for 36 days in 2021, compared to 45 days in 2020.
However, the overall situation is getting better as more companies partner with third-party cybersecurity firms, and government agencies and cybersecurity companies often notify victims of attacks, resulting in faster detection.
One more positive trend: let me remind you that we wrote that During five years of operation, the No More Ransom project helped to save $900 million from ransomware.
According to the Mandiant M-Trends 2022 report, companies have significantly improved the time to detect cyber threats over the past decade, reducing it by almost 20 times (from 418 days in 2011 to 21 days in 2021).
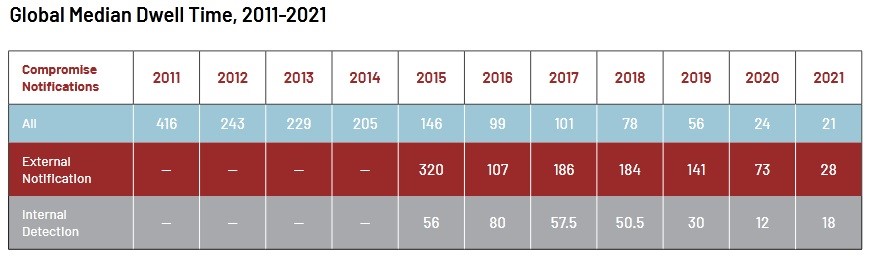
The improvement in companies’ ability to detect cyber threats varied significantly by region, with companies in the Asia-Pacific region experiencing a sharp reduction in so-called “wait time” to 21 days in 2021, compared to 76 days in 2020.
European companies also saw a significant drop to 48 days from 66 days in 2020, while North American cyber threat detections stably consisted 17 days.
By the way, did you know that: FireEye said that there are more than 1900 active hacker groups in the world.
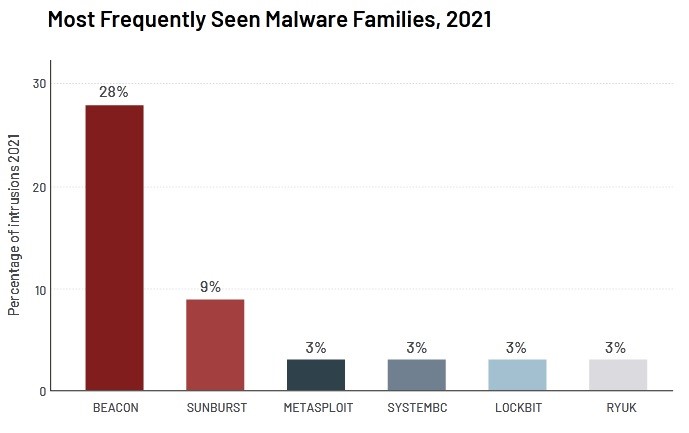
The Beacon backdoor remains the most popular attack tool for cybercriminals, accounting for 28% of all detected types of malware. Beacon is a component of the Cobalt Strike tool, which is also popular with attackers.
Exploitation and supply chain attacks account for 54% of all attacks with an identified initial infection vector in 2021, compared to less than 30% of attacks in 2020, according to experts.
Another trend is that attackers are increasingly targeting hybrid Active Directory (AD) installations because misconfigurations in the hybrid identity model, where credentials and keys are synchronized between on-premises AD and Azure Active Directory in the cloud, lead to an increased risk of compromise.












