Expert Investigated Vulnerability in Snort Intrusion Prevention System
Security firm Claroty Uri Katz has published details of a now patched vulnerability in Snort’s intrusion detection and prevention system that could cause a denial of service (DoS) and render the system useless to reflect malicious traffic.
Vulnerability CVE-2022-20685 was rated 7.5 out of 10 on the threat rating scale. The problem is present in the Modbus preprocessor of the Snort discovery engine and affects all releases of the system up to version 2.9.19, as well as version 3.1.11.0.
Information security vendors also have annoying bugs, for example, we wrote that ESET fixed a serious vulnerability in its products for Windows, and also that Zloader Trojan Disables Microsoft Defender on Victims’ Systems.
The Cisco-supported open-source Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) Snort analyzes network traffic in real time for signs of possible malicious activity based on predefined rules.
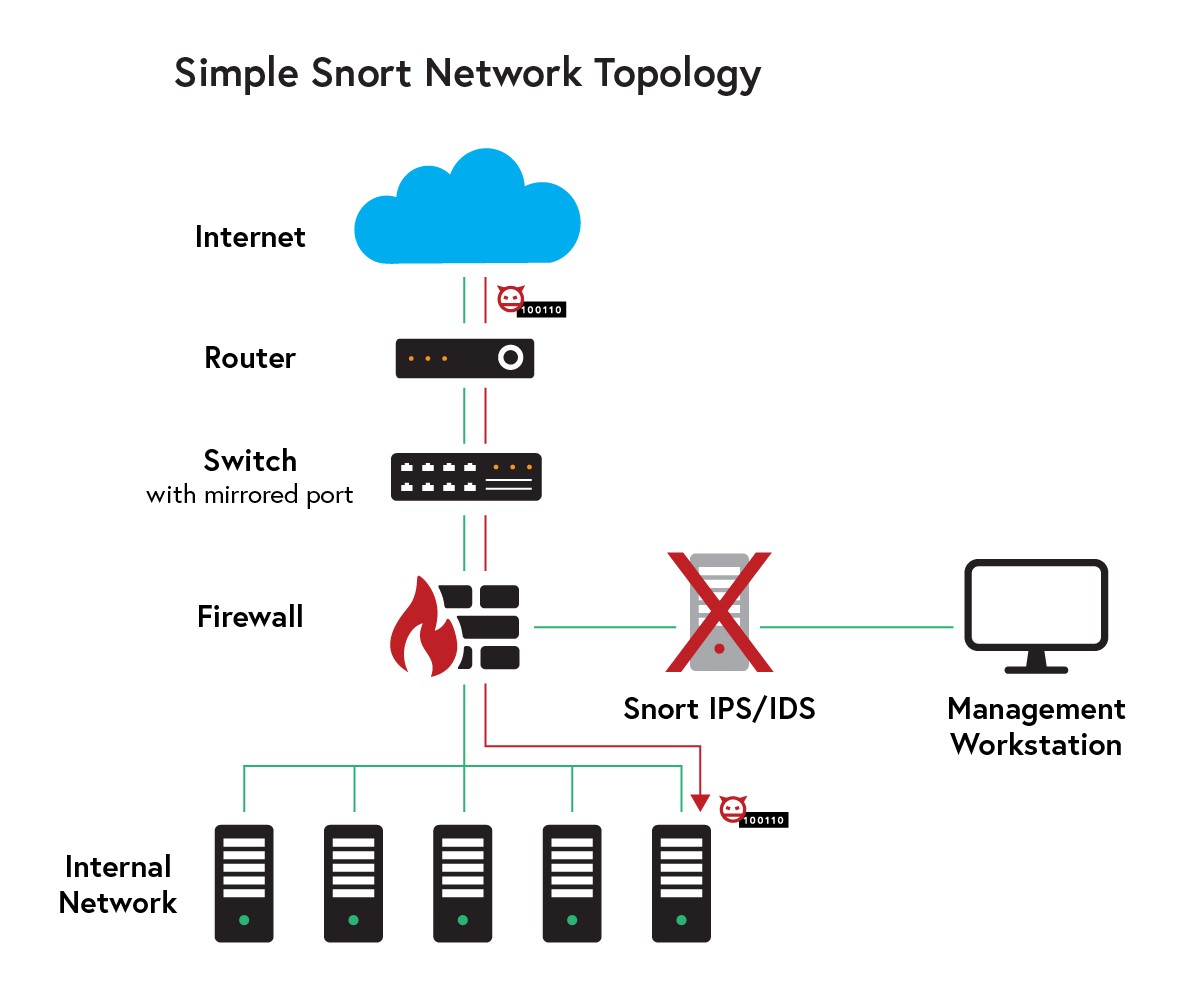
CVE-2022-20685 is an integer-overflow vulnerability. With it, an attacker can cause Snort to stop processing new packets and generating security notifications.
The problem is related to how Snort handles Modbus packets (an industrial communication protocol used in SCADA networks). An attacker could send a specially configured packet to a vulnerable device and cause Snort processes to hang.











