Hackers leaked credentials of 500,000 Fortinet VPN accounts to the public
Researchers report that a Fortinet VPN credential list of nearly 500,000 usernames and passwords is being distributed on hacker forums.
These credentials were allegedly copied from vulnerable devices last summer. The attackers say that the vulnerability used to collect information has already been fixed, but many of the credentials are still valid.
Bleeping Computer writes that the list of credentials was released free of charge by hacker Orange, who is the administrator of the recently launched hack forum RAMP and a former operator of Babuk.
Previously, due to disagreements between members of the hack group Bubuk, Orange separated from the team to found RAMP, and is now believed to represent the new ransomware Groove. This theory is supported by the fact that the leak advertisement was also posted on the Groove site.
Both of these messages contain a link to a file hosted on a darknet site that Groove operators use to host stolen data from victims.
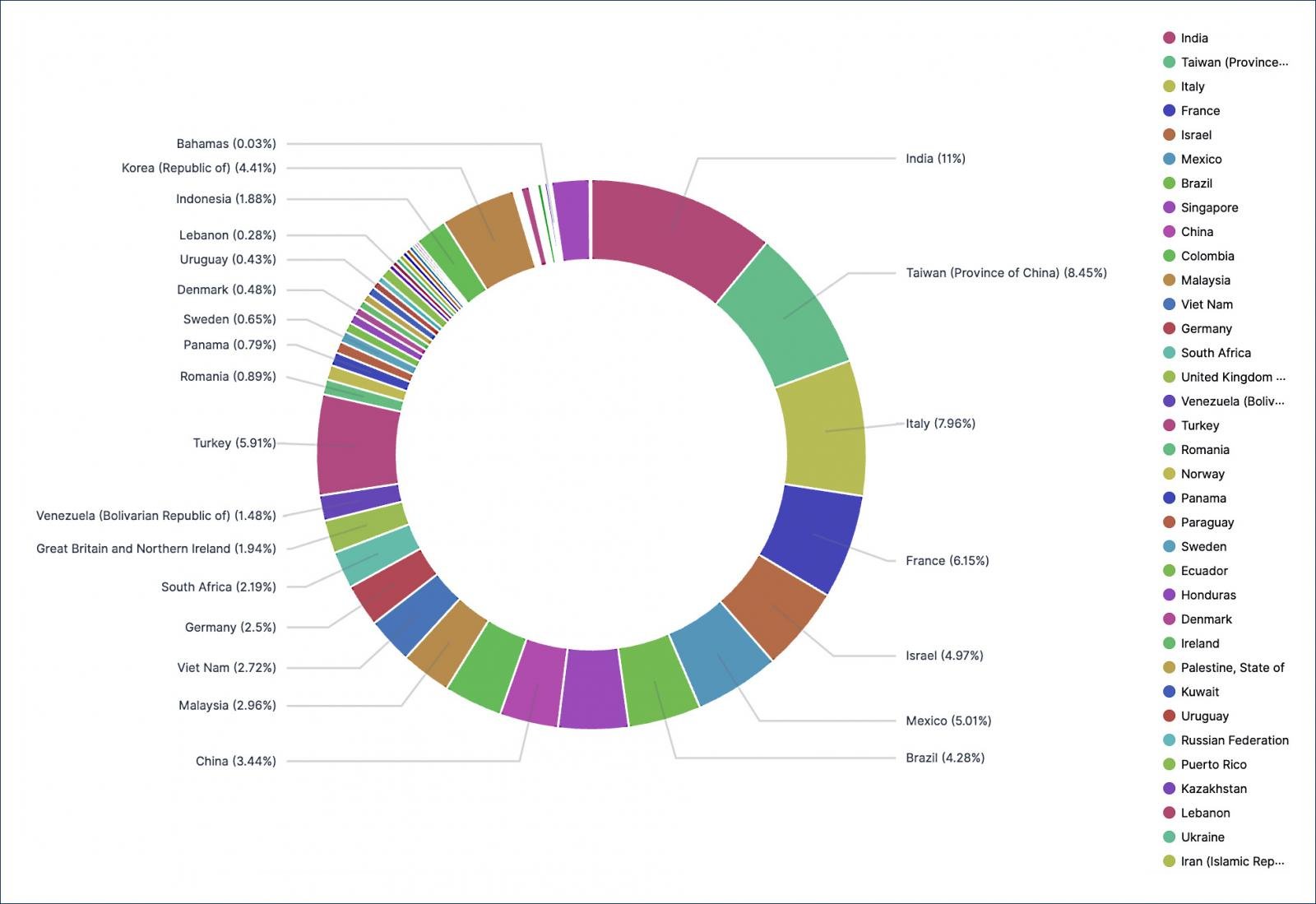
Bleeping Computer’s analysis of the list found that it contained the credentials of 498,908 users on 12,856 devices. Although the researchers did not verify that these logins and passwords worked, the publication confirmed that Fortinet VPN servers were found behind all the verified IP addresses.
Further analysis by Advanced Intel experts showed that IP addresses belong to devices around the world, of which 2,959 are located in the United States.
Information security expert Vitaly Kremez from Advanced Intel believes that hackers used the old problem CVE-2018-13379 to collect data, which was fixed by Fortinet developers back in 2018, but not all updates have been installed so far. By exploiting this vulnerability, remote and unauthenticated attackers could gain access to system files using specially crafted HTTP requests.
It is not yet clear why the attackers chose to publish the credentials for free, rather than sell them or use them themselves. This is believed to have been done to promote the RAMP Forum and RaaS Groove.
Let me remind you that I also talked about US authorities warned of attacks by APT groups through vulnerabilities in Fortinet FortiOS VPN.










