Commercial Cybersecurity Products Use Others’ Codes without Permission
Patrick Wardle, a well-known macOS security expert, founder of the Objective-See Foundation, at the Black Hat 2022 conference together with his colleague Tom McGuire, an information security researcher from Johns Hopkins University, spoke about the fact that commercial cybersecurity products use other people’s code and algorithms without permission.
Let me remind you that we also reported that LockBit Ransomware Uses Windows Defender to Download Cobalt Strike.
Wardle cited his OverSight tool as an example. This tool, offered for free by the Objective-See Foundation, allows users to control the microphone and webcam on a Mac, alerting them each time the microphone is activated or a process is accessing the camera.
The purpose of the research was to encourage other developers to find out if their code has been stolen. The fact is that researchers believe that the practice of intellectual property theft is much more widespread than is commonly believed. At the same time, Wardle emphasizes that in order to detect such a theft, you will need not only the software developer himself, but also a competent reverse engineer.
As a result of the investigation, the researchers found that at least three information security tools developed by three different companies used OverSight algorithms without permission. It is emphasized that OverSight has been available for free since 2016, but it became open source only in 2021. That is, until recently, reverse engineering this development in order to create commercial products was not only unethical, if not illegal.
Using Google and Yara’s rules, the researchers identified commercial products that use the same method names, paths, strings, undocumented registry keys, and parsing logic as OverSight.
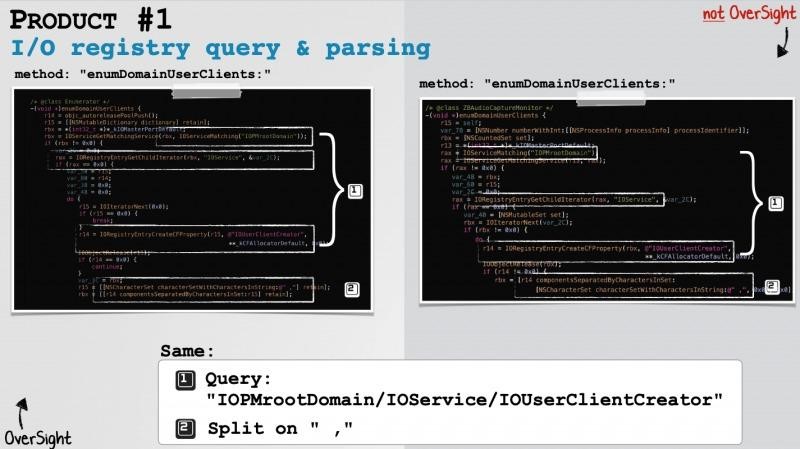
As a result, the violating companies were contacted and provided with evidence that OverSight algorithms were used in their products without permission. The companies acknowledged the problem (although one firm only paid attention to the researchers after realizing the possibility of a huge backlash from the community), promised to remove the code, and even offered financial compensation.
Wardle said the compensation offered by the companies was worthy, even if it was only a “drop in the ocean” for them. The proceeds will be used by the Objective-See Foundation to host the Objective by the Sea conference, books, and free tools.

Patrick Wardle
Although the experts did not disclose the names of companies that used OverSight’s algorithms without permission in their report, Wardle clarifies that these were both small and larger businesses. According to him, they used the stolen intellectual property in various products, including both simple utilities and more serious macOS security solutions. At the same time, most of the violators were specialized information security companies.
On the other hand, Wardle notes that in most cases the violations were the work of just one developer, and this can hardly be called “malicious corporate intent.”