Hack group FIN7 created a fake company to search for and deceive information security specialists
Information security specialists Gemini Advisory (a division of Recorded Future) discovered that the well-known hacker group FIN7 created a fake information security company Bastion Secure in order to find and hire researchers “for work”. As a result, the talents of the specialists recruited in this way were used to carry out ransomware attacks.
Bastion Secure’s website claims that the firm provides penetration testing services to private companies and public sector organizations around the world. However, experts write that FIN7 uses Bastion Secure as a screen for finding and hiring information security specialists for various positions.
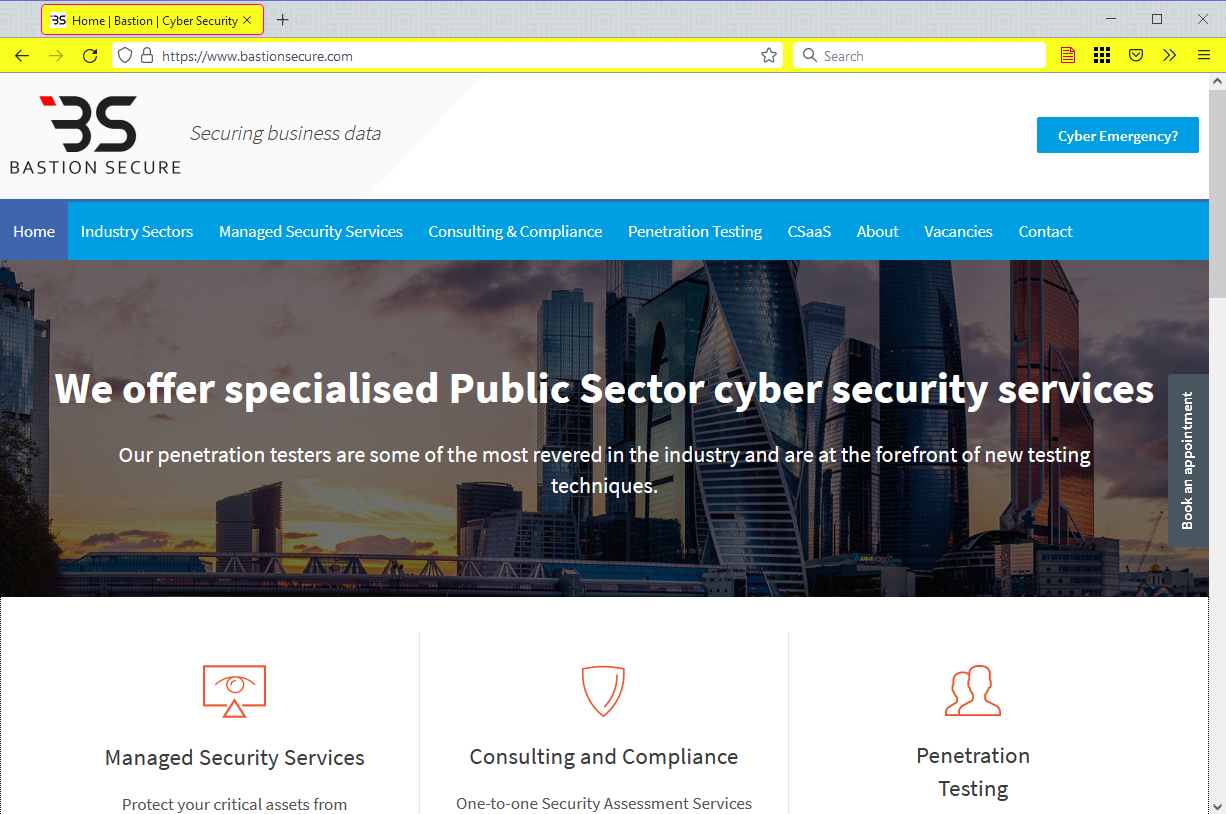
Relevant job advertisements were found on a number of Russian and Ukrainian portals (1, 2, 3…). Also, an advertisement on the hacker site (archived version) stated that FIN7 was recruiting reverse engineers, system administrators, C++, Python and PHP programmers.
Applicants who responded to such vacancies went through a three-stage interview, says Gemini Advisory, and one of its partners went through this entire process in order to study the activities of the dubious company.
- Stage 1: The first stage involved a basic HR interview, which was usually done via Telegram. If the interview was successful, applicants were asked to sign a non-disclosure agreement and set up their computer by installing multiple virtual machines and opening specific ports.
- Stage 2: In the second stage, candidates received legal pentesting tools from the company to perform a series of test tasks.
- Stage 3: Applicants were invited to participate in a “real” assignment where they were instructed to conduct a penetration test of one of Bastion Secure’s clients.
The Gemini Advisory analysis report emphasizes that in the final stage of the interview, applicants were not provided with any explanations or legal documents to authorize penetration tests, as is customary in such cases. In addition, Bastion Secure representatives advised candidates to use only certain tools that would not be detected by security software and specifically look for backups and file storage systems on target companies’ systems.
The tools Bastion Secure supplied Gemini Advisory insider turned out to be linked to malware such as Carbanak and Lizar/Tirion, which has long been considered part of FIN7’s arsenal. In addition, the tasks and operations in the interviews were “consistent with the steps taken to prepare for ransomware attacks.”
In the course of these attacks, ransomware such as Ryuk and REvil have been identified, which have been linked to FIN7 in recent years, according to the researchers. According to Microsoft experts who also tracked the fake FIN7 company, newer attacks would have deployed the ransomware DarkSide and BlackMatter. So, recently, speaking at the Mandiant Cyber Defense Summit, Nick Carr and Christopher Glayer from Microsoft said that FIN7 not only used the Darkside ransomware (and its later rebranding BlackMatter), but also independently managed Darkside RaaS (Ransomware-as- a- Service).
Interestingly, creating a fake information security company is not a new tactic for cybercriminals. The FIN7 group was already doing the same in the mid-2010s, and then the hackers were running another fake information security firm – Combi Security. At the time, FIN7 was mainly dealing with Point-of-Sale malware, so Combi Security hired penetration testers to hack into retail chains. Thus, a PoS malware was deployed in the networks of compromised firms to collect payment card data from compromised networks.
The researchers say that the creation of the second fake company is very simple, it is connected with the operating costs and finances of the hackers. The reality is that it is cheaper for a hack group to find and hire a third-party information security specialist than to work with other hacker groups or individuals hired through underground forums.
For example, according to Gemini Advisory, an information security specialist in Russia usually earns between $800 and $1,200 a month, while criminals are likely to claim a percentage of the ransom received as a result of a ransomware attack. Indeed, in some cases, the ransom can easily reach several million US dollars.
Let me remind you that we also wrote that Fake antivirus promised protection from Pegasus spyware, but turned out to be a Trojan.