Target Open-Source Web Skimmer Scanner
Target (one of the largest e-commerce retailers in the US, which also owns a supermarket chain) has open-sourced an internal Merry Maker tool that the company has been using since 2018. The scanner allows determining whether the site has been compromised and whether it contains malicious code that steals customer payment card data.
Let me remind you that web skimmers are also called MageCart attacks. Initially, the name MageCart was given to one hack group, which was the first to inject malicious code into websites in order to steal bank card data. As part of such attacks, hackers break into websites and then inject malicious code on their pages that records and steals payment card information that users enter during checkout.
The previously proprietary Merry Maker was built to work with e-commerce portals and behaves like a real user: it can browse product pages, search for specific items, add products to the cart, and enter payment details on the checkout form.
At the same time, Merry Maker checks in real time how the resource reacts to all these actions, and performs continuous analysis of any code that the site loads and executes. All code is matched against lists of known indicators of compromise and YARA rules for known threats. For example, domain names, IP addresses, and JavaScript files are matched against those previously used in web skimmer attacks. When it detects a problem, Merry Maker warns you about it in a message on the control panel.
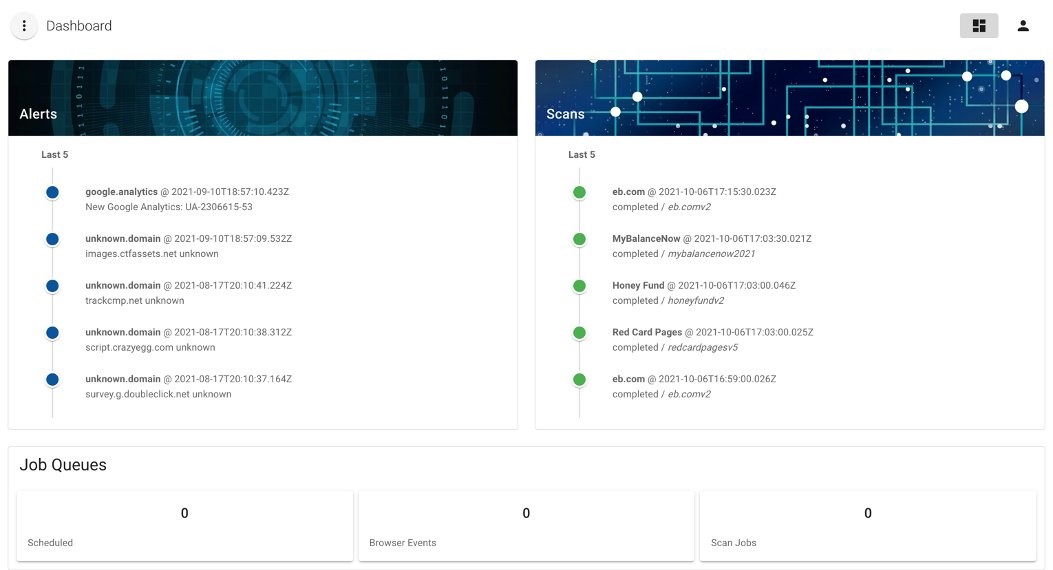
The Merry Maker code is already published on GitHub.
Let me remind you that we also wrote that Comodo will open endpoint detection and response (EDR) product source code, and also that Canon sends instructions to customers on how to bypass their own cartridge protection.











